Hackers use social networks to hack credit cards
The techniques for attacking users of digital services are varied.
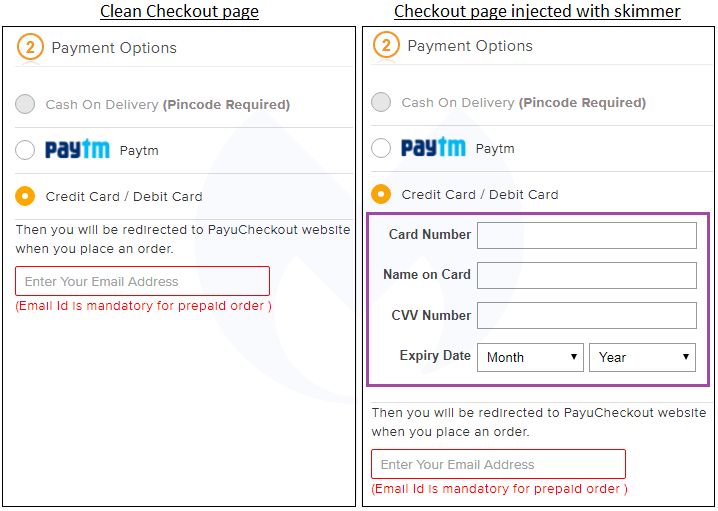
As we know, every time you access an online service, you endanger not only your data but also your wealth. Recently it was discovered that cyber criminals could use social media buttons to initiate computer attacks. This is thanks to a new type of malware that can be used directly on the web. This malware can hide inside images, which are used for certain buttons such as sharing on social networks. Its feature allows hackers to steal information from credit cards entered into online payment forms, uses said infected button.
This article will also interest you: Fraud in banking transactions
This malware is called the "Magecart script" or "web skimmer." The Dutch computer security company called Sanguine Security (SangSec) made its discovery last September on some online shopping sites.
The technique used by hackers, in the context, is known as shorthand. It is a method that allows hackers to hide information in another format, such as text in images or videos or images in videos. If the technique was not initially used for cybercrime, hackers use it to hide malicious codes in formats that would normally go unnoticed in front of security scanners. In making history of this practice in the cybercrime sector, it has been observed that hackers have tended to initiate forms of attack by hiding malware inside some image files often in JPEG or PNG format.

Going back to web skimmer, the shorthand process does work, as the majority of computer tools used are usually hidden in JavaScript code. Unlike the practice of hiding malicious charges in images. The tactics of web Skinners are widely adopted by hackers who can then use them to hide malicious codes in the logos of websites
"As the use of shorthand has grown, security companies have also begun to search and analyze image files for irregularities. The interesting detail of these recent attacks is that the malicious code was not hidden in PNG or JPG files but in SVG files, a type of image file for loading vector images. The cybersecurity company explains. However, SangSec acknowledges that cybercriminals were smart enough to have used shorthand in such a context. "The malicious payload takes the form of an HTML < svg > element, using the item as a < path > container for the payload. The payload itself is concealed using a syntax that looks a lot like the correct use of the < svg > item," read a report published last week by SangSec. The Dutch company adds that:
"While hackers have added their malicious payload to files like images in the past, this is the first time that malicious code has been constructed as a perfectly valid image. The result is that security scanners can no longer find malware by simply testing the valid syntax."
SangSec added that it had detected cyber criminals last June when they were testing their malware on websites. It was the same during the month of September, "with the malicious payload hidden in social media sharing icons for sites like Google, Facebook, Twitter, Instagram, YouTube and Pinterest. SangSec notes.
Therefore, vigilance is required. Users are encouraged to be very careful when making their various online transactions. They can contact specialists to help them get around this problem. The use of antivirus or any other security solution is also recommended.
Now access an unlimited number of passwords:
