Hacking a Snapchat account: how do you go about it?
Have you ever tried to initiate an attack to hack a Snapchat account?
We are going to give you some tips that will help you so this article. However, we would like to make an important clarification: is computer hacking an act prohibited by law. In other words, any attempted action that targets the account of others without their authorization is liable to legal proceedings.
This article will also interest you: Hack Snapchat: how do hackers do it?
Therefore it is possible for you to try your hacking technique on yourself or on the account of a loved one with his consent. If you are a parent, obviously you need to watch your child. Here are some tips that might help you:
1- Use software to find the password
In the list of methods that we are going to offer you, we want to start with the one that is most suitable for beginners in hacking. This involves, among other things, using software to find the password. You are probably wondering why the password?
A Snapchat account requires two types of information to access it: First, you have the username ID which is either the email address or the phone number. Usually users tend not to hide this information. Because most often it is data that is used almost everywhere, especially in our daily exchanges. So if possible and a Snapchat account in particular, for example that of your child, finding the phone number or email address is a breeze. You don’t have to be a hacker for this.
The second information to access the Snapchat account and its password. This is where things get complicated. Indeed, it is not easy to find the password of an account so easily. Because it is the most important authentication data. In other words, one should therefore expect to employ unorthodox methods. So how do you do it?
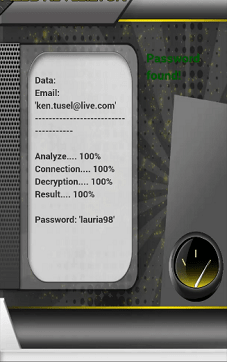
To find the password we suggest PASS DECODER. It is a SIMPLE-to-use computer program. And in a few clicks you will be able to obtain the password you are looking for.
How does this software work?
PASS DECODER is a computer program compatible with several types of media. In other words, you can use it either on a smartphone, on a digital tablet or even on a computer. In addition, it is compatible with the various most used operating systems, namely iOS, Windows and Android.
In three simple steps, here is how to proceed:
– First, you just need to download it first;
– Then you install it on your terminal;
– You launch the search for the password of the targeted Snapchat account. This search is done using the email address or phone number associated with the account.
The result is guaranteed to you after a few minutes. And then you will have all the information you need to legitimately hack a Snapchat account without the knowledge of its user.
You can download PASS DECODER from its official website: https://www.passwordrevelator.net/en/passdecoder
By the way, the new user you have 30 days of testing. At the end of these days of testing, you are either satisfied or your money back.
2- Use a Trojan horse

A Trojan horse is a computer program that is typically used by cybercriminals to perform several types of cyber attacks. These actions include espionage, the theft of personal data and the taking of control of the targeted terminal remotely.
The Trojan horse is software that installs itself behind a legitimate application. In this way, it gives its operator the possibility of being able to initiate the actions that we have mentioned above. However, it should be mentioned that the use of Trojan horse is generally reserved for people with a strong knowledge of hacking. Therefore if you are an amateur it is much more difficult for you to be able to do this. First, you will need to get some, which in practice is not an easy task. Then you’ll need to make sure you can use it without it backfiring. Therefore it is a method which presents more risk for you than more.
3- Hijacking

The Hijacking, a method of fairly complex hacking. It is mainly intended for professionals and for people who already have a good experience in the practice of hacking. This technique consists in particular in diverting the Internet user’s communication to another point of contact in order to:
– To spy on him;
– Steal their personal data;
– Hijack his communications.
There are several variations to this practice. Indeed, Hijacking can be practiced when the targeted person lets himself be hijacked by a fake WiFi network. Most often, cybercriminals deploy fake WiFi hotspots, in order to initiate session hijacking. They can also use it to initiate another well-known form of Hijacking, the man-in-the-middle attack.
In practice this is a technique, which is not suitable when you are a beginner in computer hacking.
Now access an unlimited number of passwords!