How to set up a fake public WiFi hotspot?
Today updating the wifi network is becoming more democratic.
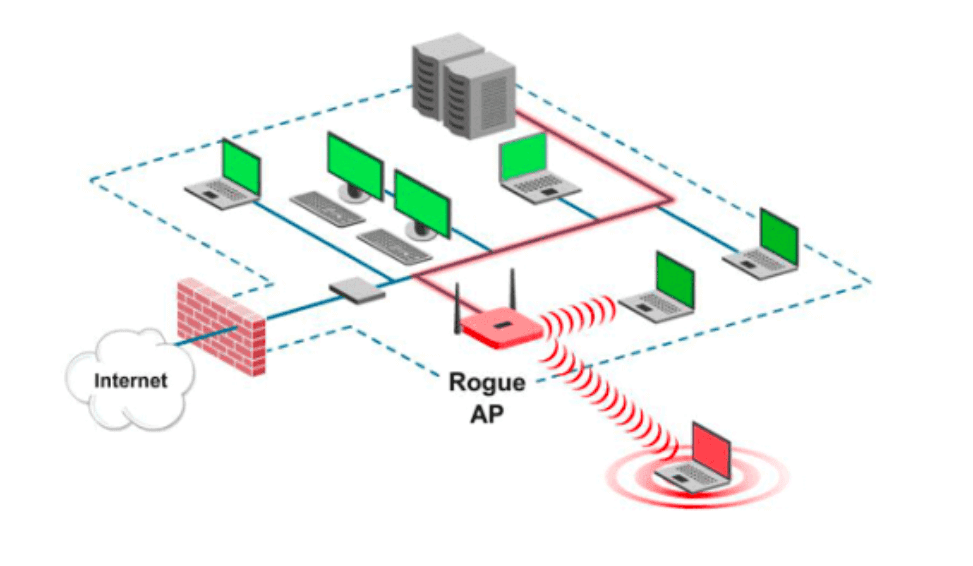
It is not uncommon to find networks available in public places or even in workplaces. The problem with WiFi is not its great accessibility or the ease of being able to share the Internet connection, it is rather the dangers that could hide behind this technology.
This article will also interest you: How to hack a WiFi network?
Indeed, many of us generally connect to WiFi, seek to ensure the authenticity and security of this network. However, there is a high chance that they will be used by people with bad intentions to either spy on us or steal personal information, login credentials, or be able to install malware in our terminal.
You are probably wondering how this can be possible. Simply create a fake WiFi network. Can you really create a fake WiFi network?
The question is yes. It is totally possible. In our article, we will describe the procedures generally used by people to set up fake free hotspots, the use of which is not always legitimate.
We would like to remind you that the content of this article is purely for educational purposes. You are therefore advised not to use it in situations that could be contrary to the law. Just make sure you understand the process and protect yourself from now on every WiFi connection.
What you need to know as a prelude is that to make a fake WiFi network, you do not need to have exceptional computer skills or hacking. You will have to settle for the basics and some knowledge in the material.
Let’s talk about the material, you need some special tools that are not difficult to obtain. In any shop selling computer products, it is possible to have its elements which are among others:
1 – a Raspberry Pi (Pi 1 model B+)
2 – ALFA Network antenna (AWUS036HNA)
3 – xtorm battery (AL390) (battery power will depend on long-term or short-term use. Ways to practice even a 2500 milliamp battery with USB output can do your little experiment.
In addition to physical equipment you will also need some computer programs which are also very easy to obtain. Those are :
1 – raspbian
2 – hostapd
3 – dnsmasq
4 – lighttpd
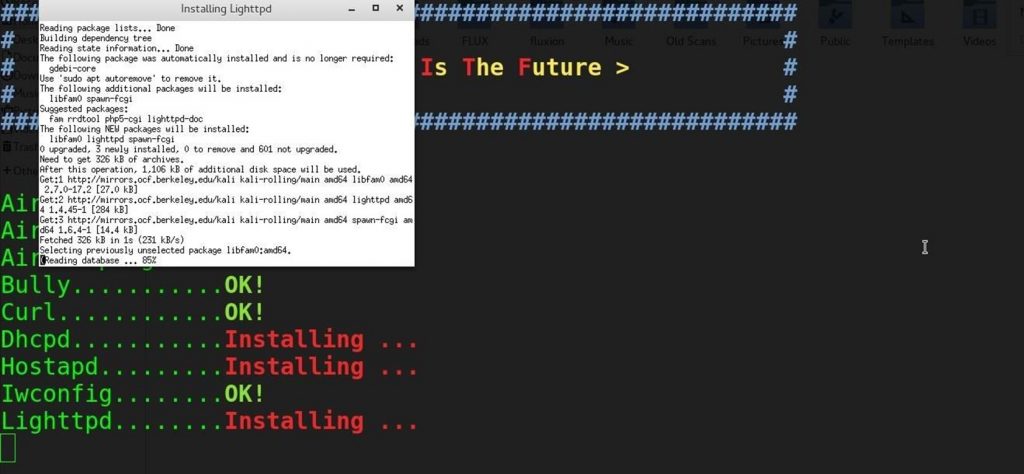
As we mentioned above, these software are easy to get hold of. Indeed they are all open source and you have the possibility to download it by the Apt extension, so you will not need to do any other configuration.
Once all this is together, you simply need to configure the hardware. Note that for all the installations and the preparation there is or simply nothing extraordinary to put into practice.
– First you need to install a Linux distribution. Most often, specialized hackers use a Debian distribution, which is generally adapted to the Pi. As for the complete installation procedure of Raspbian, it is possible to have tutorials available on YouTube Google. You just have to type “installation of the Raspbian distribution (in French or in English)”.
– Then you need to create a fake login page. This fake login page will be used to see and monitor all login attempts made through a mobile phone. Obviously the usefulness of such a page and to be able to collect connection data.
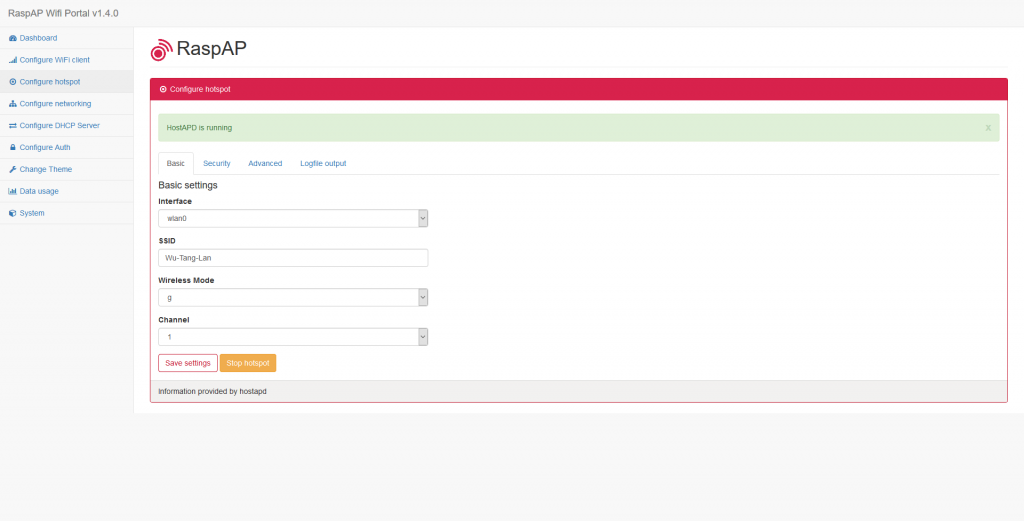
– Use “hostapd”: it is a network utility whose basic functionality is to facilitate the execution of several technical tasks when creating a wifi access point. It easily allows configuration of the wifi card allowing devices that are looking for an access point to connect. It also allows the transfer of connection information for DHCP-type devices. It also facilitates the use of dnsmasq, which will help intercept either some or all of the DNS traffic.
– Use “lighttpd”: it should be noted that the latter is a web server. It has the particularity of being quite light and is perfectly suitable for machine operation and there is low power such as a Raspberry Pi 1. It will then allow a dummy login page to be transmitted to other devices which connects to the network oven. With each HTTP error, traffic is captured and drafted to the fake homepage to be created.
– Finally, capture the connections. Once all these processes have been completed and the hardware assembled and software configured, you can then begin your login capture work.
Now access an unlimited number of passwords:
