NotPetya – understanding the global cyberattack in 6 questions
On June 27, 2017, computer systems around the world met a new malware called NotPetya.
The attack begins in Ukraine's epicenter, and then spreads around the world. It is one of the most devastating cyberattacks the world has ever seen.
This article will also interest you: Ransomware: Maersk says he has learned an important lesson in his fight against NotPetya
Today in 2019 we will try to make a new understanding of this problem and try to better understand it. Through a relevant analysis conducted by the security company Kaspersky, we will understand the case in 6 questions.
1- What happened?
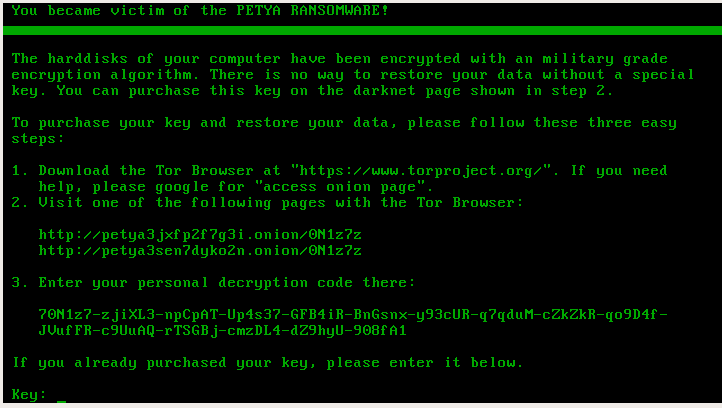
all June 27, 2017, 65 countries around the world, from around the world, millions of infected terminals Ransonware-type malware. Ukraine, the epicentre of Russia are the two countries most affected. Some large French companies also suffered the blow of this particularly Saint-Gobain and SNCF, which led to the opening up of an investigation by the Crown.
According to Kaspersky's analysis, when the computer or a training system is infected with the NotPetya malware, it encrypts the computer data of this terminal based on the algorithms AES 128 and RSA 2048. The computer is blocked. A message appears on the screen asking the user to $300 in Bitcoin format.
2- How is this attack named?
Several names have been circulated. But in the end, they all finished by opting for the name known today "NotPetya" to detach it Petya malware from which it draws a few straps of code.
3 – How the terminals were infected with NotPetya ?
Like its predecessor WannaCry, the NotPetya was a particular target for companies and Organizations. Unlike WannaCry, it is not transmitted via the Internet messy way. According to Microsoft, it is essentially based on a update procedure developed for accounting software, 'MEDoc', to bring malware into systems companies. Kaspersky also discovered that there was another that allowed programs to spread. This vector is the official website of a Ukrainian city Bakhmut in the Donetsk region. The home page of the site internet has been corrupted by hackers in such a way that any anyone accessing it automatically downloaded a camouflaged executable under Windows update form.
4 – How does it spread through a computer network?
Once this program infects a machine within a company affiliated with the this one, he's going to try to spread using the internal network in order to trap others machinery. To achieve this, NotPetya will use hacking tools that were stolen from NASA, then published by a group of hackers called ShadowBrokers. These tools control are called EternalBlue and EternalRomance. And in principle, their function is to allow you to control a machine using fairly good protocols especially. The advantage of using its tools is that it will allow the program to be able to take control of a machine even if the machine updates, which is supposed to make it easier to take control
5- Is the data recovered once the ransom is paid?
Not. Since the German host Posteo deactivated the email address identifying those who are making the payments, it was impossible for hackers to know who to send the script to decipherment. This makes the process totally inoperative. which is to say that even if hackers intended to return the encrypted data, they couldn't have. However, according to cybersecurity researcher Matt Suiche, the ransom message was merely a façade because apparently the real purpose of this hacking was the sabotage. According to his analysis, the hard drive of the terminals corrupted by the program was unrecoverable because the data did not appear to have been backed up any part. "The current version of Petya has been rewritten to be a wiper, not ransomware," explained the expert.
How can we protect yourself from it?
The virus could be detected from a moment by almost all antivirus solutions. on the other hand, it is impossible to stop the spread if network administrators decide to block SMBv1 traffic and some of the administrative tools including PSEXEC and WMIC. In addition, it was discovered by a computer security researcher named Amit Serper, a file, which once present on the terminal prevented the NotPetya program from running properly.
Now access an unlimited number of passwords:
