PASS ACCESS is the legitimate and certified ISO 9001:2015 & ISO/IEC 27001:2022 AI-powered application that allows you to quickly hack one or more Yahoo! Mail passwords and then log in to them.
Without PASS ACCESS, you’ll never succeed! Imagine being able to quickly bypass protections and connect a Yahoo! account even when it’s secured by a password. Discover the full power of this solution right now.

Take advantage of this simple trick—you’ll be amazed by the results! With PASS ACCESS, you can recover as many passwords as you want with no usage limits and from anywhere in the world!
Don’t waste any more time! Your contact emails could be at risk and lost forever if you can’t access your Yahoo! account. If you don’t have the password for your Yahoo! email address, PASS ACCESS can easily extract it for you in just a few minutes even if the account is old.
Although password extraction is typically a complex and time-consuming process, PASS ACCESS simplifies it using a powerful artificial intelligence algorithm that incorporates real-time data interception and analysis. Combined with a sophisticated cryptographic password-breaking script system to deliver accurate and efficient results, the access code is placed in the broadcast variable. Then, based on the results from the protected database storage, the Yahoo! password is displayed clearly on your screen.
PASS ACCESS’s sophisticated method does not generate any Yahoo! alert notifications throughout the process.
![]() WARNING: Only use this application on an account you are authorized to access. Please review the terms of use.
WARNING: Only use this application on an account you are authorized to access. Please review the terms of use.





TRY IT NOW!It’s a piece of cake—no technical skills required to get started... PASS ACCESS represents the solution to a problem many users have already faced: gaining access to an account! To start decrypting Yahoo! passwords, please follow these 3 steps:
Have doubts or questions? Contact us without hesitation or try it now with a 30-day money-back guarantee! We’re confident in our application’s effectiveness, which is why we’ll issue a refund if it doesn’t work. Start NOW and immediately access passwords Frequently Asked QuestionsWho can use PASS ACCESS?PASS ACCESS can be used by anyone who wants to recover passwords for Yahoo! email accounts. However, please comply with the laws in your country and only use this application on accounts you are authorized to access. Is PASS ACCESS secure?Yes, PASS ACCESS is safe to use since no external information is communicated. How many passwords can PASS ACCESS hack?There is no limit. PASS ACCESS can recover as many Yahoo! passwords as needed. How long does it take to get results?PASS ACCESS retrieves passwords in just a few minutes by leveraging vulnerabilities in protected database storage. Does PASS ACCESS store recovered passwords?No, PASS ACCESS does not store recovered passwords to ensure user privacy and security. All data is cleared when the app closes. Is using PASS ACCESS confidential?Yes, PASS ACCESS does not require account creation or personal details to operate. Does PASS ACCESS work in my country?Yes, PASS ACCESS is designed to work globally, allowing users from different countries to access its features. Is there a trial period for PASS ACCESS?Yes, PASS ACCESS offers a trial period with a 30-day money-back guarantee. You can test the application’s effectiveness. If it doesn’t work, simply contact us for an immediate refund. Does it require a monthly subscription?No, PASS ACCESS is a one-time purchase. No monthly subscription is required to use the application. How long does it take to receive it after payment?PASS ACCESS is available immediately after payment. There is no waiting period to download the application. Is it legal to use PASS ACCESS?It’s important to comply with the laws in your country regarding the use of PASS ACCESS. Only use this application on accounts you are authorized to access. |
PASS ACCESS is the most powerful application that allows you to recover your Yahoo! email password and regain access to all your contacts. Please respect your country’s laws and do not use this application to access accounts that do not belong to you.
Finally, a solution you can use without restrictions to access your contacts and passwords. Start your PASS ACCESS trial now and log in quickly. Money-back guarantee!
With PASS ACCESS method no knowledge is needed, it is the only exploit on this website that will usually provide you with full access to your Yahoo! account with the webmail address you provided us. We help people who are looking for a way to enter the social network to achieve it.
If you are one of those persons, we will solve your problem quickly and easily. We offer clean and professional services that help you hack Yahoo! accounts. This tool is to be used to recover and change your own secured Yahoo mailbox that you need to access, to help your friends recover their password with their permission or for parents to keep an eye on their children's accounts.
Nothing is more painful than being hacked into Yahoo account. People taking control of your account usually do not have good intentions and this violation of your privacy can be hard to live with. Between confidential correspondence and false messages posted in your place, the situation can quickly degenerate. So, how do you do when someone hacks your Yahoo account? How much does a hacker make? Many have already asked the question, hoping to see a career plan outlined. Even if all hackers are not malicious, many seem to make a good living.
According to one study, a spammer can earn up to $2 million a year! When we are kids we all dream of becoming a pilot, singer, actor or footballer. But did you know that a Yahoo hacker could make a better living than some football players? Indeed, a hacker spammer can earn $100,000USD per month!
Hackers always find ways to achieve their ends. Here is a small list of hacking methods that allow hackers to crack Yahoo! accounts.
Secret question hacking is a method used by hackers to take control of Yahoo! accounts online. They find personal information about the victim like the name of their dog or mother, then create a fake site or send a fake message that appears legitimate. They ask the victim to answer security questions. Once the answers are obtained, the hacker can access the Yahoo! of the victim.
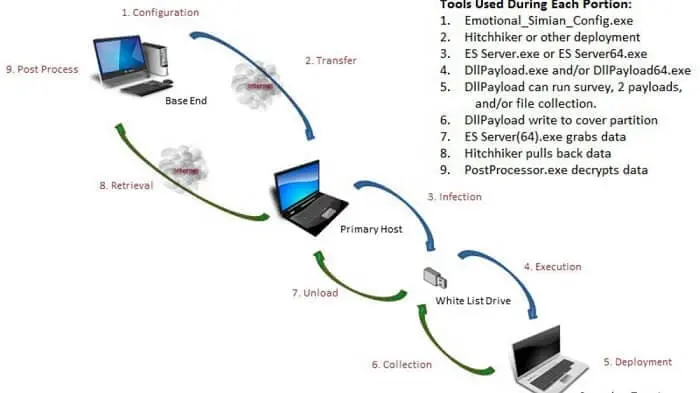
It is possible to hack computers that are not connected to the Internet. Naively, you think the best way to preserve your computer from any attack is simply to cut off access to the Internet.
It's overlooking the fact that it's possible to hack the computer manually, simply by plugging a key or a hard disk into the USB port. This is one of the strategies used by the CIA to access information.
Using a program, the CIA would be able to remotely access many data, using a Yahoo hacker tool that is installed on a computer worthy of interest. It infects any connected USB device. When the key was then plugged into a computer without an Internet connection, it infected it with one or more malicious software depending on the mission.

Some hackers managed to hack data remotely, with a drone. It was enough for them to observe the blinking light of LED of the hard disk of a computer yet completely isolated from the Internet.
To succeed in their exploit they used a modified drone with a special sensor and managed to infect the secure computer with a special malware. Isolating a computer full of sensitive data is no small matter. It is necessary to cut it off the internet, put it in a special room that isolates any electromagnetic radiation. Ensure that the room is also insulated at the sound level and now also that the room in question does not have a window. Hackers have just proven this by deceiving the security of an air-gap-isolated computer containing sensitive files.
Previously they introduced a malware into the equipment what one imagines possible in real situation, via social engineering. Then they created a drone equipped with a camera and a special sensor. The purpose of the malware is to take control of the LED of the hard drive to make it flash at 5800 times per second to transmit data through it. One imagines the data transmitted at regular intervals: the drone has only to fly in front of the window where the computer equipped with the malware is at a precise time and to position so as to see the LED of its hard disc. The experience shows that sensitive data can be successfully leaked via the HDD LED at a maximum speed of 4000 bits per second.
It is ten times faster than existing methods to steal data from a computer isolated by an air gap. This rate allows fast exfiltration of encryption keys, keystroke logging, text and binary files. It can be seen then that the drone can locate the LED of the hard disk and recover the signal. The drone remains hovering the time of the transfer before slipping away. The advantage of this method is that it is very discreet. Even an operator who would look at the LED on the hard disk could not tell the difference between a normal blink and a suspicious activity.

Fake instant messaging apps looking like the well-known Yahoo Messenger are being used to hack smartphones from activists, military, lawyers, journalists and others in more than 20 countries. These "clone" applications, which look like real ones, contain malware that can crack Yahoo password, take pictures or make audio recordings.
The system is very simple: it is enough so that the user who downloaded this false version without his knowledge allows the application to access the camera and microphone of his smartphone. Spyware can also recover stored personal data, such as internet browsing history, call log, SMS...
Data security is always an exciting topic because it is complex. Yahoo hackers use lots of possibilities to hack Yahoo! passwords like phishing, keyloggers, remote access... Many of them claim to attack the systems for fun, for the challenge. There are also pirates who want to make themselves known or even find a job by this means!
Finding a password has become a very frustrating exercise because you often have to go through it several times. "The password must contain an uppercase", also a figure and a punctuation character. Once your code has been entered, chances are that you will be asked to change the password within a few months for security reasons. Finally, if you have not forgotten it before... Our application PASS ACCESS helps you to find any Yahoo password!

Here are some tips to better protect your Yahoo! account. These methods that we are going to advise you are intended to better protect your account:

This method allows you to double verify your identity. When you try to log into your Yahoo! account, if you enter your login ID and password, another account will be generated automatically by the Yahoo! servers and will be sent to you either by text or email. You must use the code for the second authentication.
Sign in to your account
Log in to your Yahoo account.
Go to Account Security in your settings.
Under “Ways of signing in”, click 2‑step verification.
Choose the method you wish to use for the second step, such as:
Authenticator app (e.g., Google Authenticator, Authy, Microsoft Authenticator)
SMS code (less recommended)
Why is this so important? Quite simply because it's an extra layer you that can save you when you've been a victim of phishing or a data breach. Regarding the data breach Yahoo has been the victim of this kind of problem several times.
First and foremost, the first vulnerability of users are their passwords. You have to take care of the latter. Whether in terms of its composition or in terms of its full-time use. Avoid using your birthdays and any other personal information to formulate your password. Then don’t make the mistake of using the same password on multiple online platforms. In addition, absolutely avoid saving your passwords in your browsers when you log in. While this offers the benefit of faster connectivity, it exposes you to potential data hijacking in the event of an attack.

You may receive a link in a text message or in an email inviting you to sign in to your account. Never do it! If the need arises, go directly through your browser and access the site directly. Most of the time it is a case of phishing.

You should make sure that you always lock the computing device you are using when you are not using it. You should also equip this device with anti-virus software to protect yourself from malicious programs that steal personal data.
It is important that you monitor how things are moving on your Yahoo! account’s side. Indeed, do not wait to have an email before taking a look. Otherwise you may be surprised by potential inappropriate movements. Often try to check if nothing suspicious is happening.

No more convoluted password and full of numbers. The IT expert Bill Burr, who is responsible for standards in password, revisits the rules he has himself enacted on "safe" passwords. In 2003, a former employee of the government agency responsible for the enactment of technology standards, established a list of recommendations to protect online accounts. Among its recommendations, the use of special characters, capital letters and numbers, as well as a regular update of passwords, to slow down the work of hackers. The document subsequently became a reference in the matter. In the end, complex passwords, sometimes without logic and difficult to memorize.
These rules would now be obsolete, according to the IT Expert. The Web is now a new generation, all this was probably too complicated to understand for the majority of people, indeed, it was not necessarily relevant. "PassRevelator2000" rather than "N3v$rM1^d"? Recommendations were aimed at preventing hackers from guessing the passwords of their victims by testing all possible combinations.
However, they have had a perverse effect. By standardizing the way to create a password, they have created bad habits in many people. In particular, to put a capital letter at the beginning or a number at the end. All these practices have been integrated into their algorithms. You should learn how to create a good password.
The Web has evolved since 2003 and massive data leaks from Yahoo! have given grist to the researchers. A recent report now advocates the use of long, easy-to-remember phrases to the detriment of special-character passwords. Renewal of a password is recommended only if it is suspected that it has been stolen. A study by the British secret service had shown the uselessness of regular updates of corporate passwords. The rules recommend using passwords of at least twelve characters of different types, advocating two methods. The phonetic method, for which "they bought eight cd for one hundred euros this afternoon" will become "uozn9%xJ;".
The method of the first letters, for which the quotation "2 beers are better than one you will have" will give "1tZUE2tlS", according to two examples mentioned on the site of the institution. Passwords are also affected by fashion. Strongly recommended in recent years, password managers are now the subject of recurring debates in the field of computer security. Rich in personal data, they are a prime target for hackers. Earlier this year, some companies confirmed that they have been a victim of piracy. Our software can recover any password whether they are strong or not.
Passwords do not have to be complicated. Choosing his password, while massive hacking announcements multiply, remains a dilemma. Securing your accounts on the Internet is more than important, personal data is expensive. But it seems that the techniques used up to now do not ultimately serve much. Secure passwords are less complicated than expected. The classic tips for choosing your password are obsolete. For more than ten years, it’s been advisable to choose your password by securing it with capital letters, lowercase letters, numbers and special characters.
Furthermore, in the unfortunate event that you fall victim to computer hacking, allowing the perpetrator to take control of your account without your knowledge, we have an appropriate solution to assist you in reclaiming your Yahoo! account. We provide you with a computer program designed specifically for this purpose.
The primary function of the PASS ACCESS application is to retrieve the password of any Yahoo! account. To achieve this, it requires only the email address associated with the targeted account or the phone number directly linked to it. Armed with either of these pieces of information, PASS ACCESS grants you the upper hand, swiftly recovering the password of the compromised account in a matter of minutes.
Yair Wahal, Marketing Director, Zingali Acustics