PASS BREAKER is the certified application compliant with ISO 9001:2015 and ISO/IEC 27001:2013, taking advantage of the power of artificial intelligence capable of retrieving all passwords associated with GMail services simply from an email or an @ID (e.g. YouTube)!
Attempting to manually decode passwords seems nearly impossible. Imagine using the performance of PASS BREAKER combined with artificial intelligence as it stands as the sole method to quickly find a GMail password. You can execute this task on as many accounts as you need, without any usage restrictions!

Grab this chance with a simple hack that lets you access any account, you'll be amazed by the results! Our application has no time limits and can retrieve GMail passwords worldwide in just a few minutes.
PASS BREAKER uses artificial intelligence to exploit security vulnerabilities in GMail databases, enabling it to quickly get passwords linked to a specific profile.
To understand how PASS BREAKER works, it's important to note that its advanced technology relies on a search analysis system equipped with a script algorithm for complex and optimized asymmetric cryptographic decryption supported by a neural network:
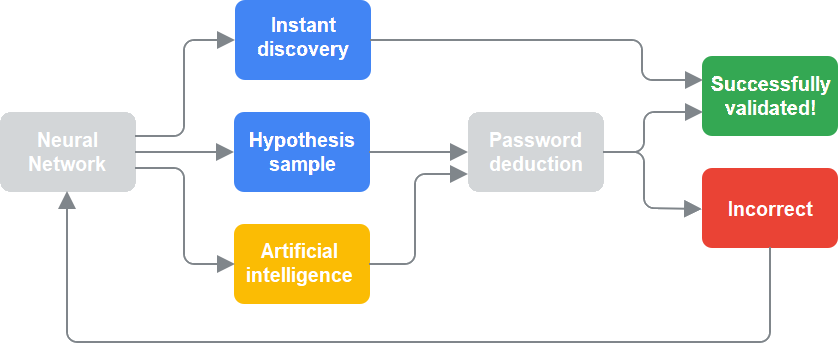
Once a password sample is validated, PASS BREAKER employs these probability formulas to deduce the complete password based on the neural network's distribution. Subsequently, it displays the password on your screen.
The straightforward approach of PASS BREAKER allows it to efficiently extract passwords from any account, exploiting vulnerabilities in databases while automatically bypassing two-factor authentication (2FA) protections. With PASS BREAKER, no notifications will be sent during the account login.
![]() WARNING: Don't
use this application on accounts other than yours without permission. Read the rules, be aware.
WARNING: Don't
use this application on accounts other than yours without permission. Read the rules, be aware.


TRY PASS BREAKER NOW!Starting is a breeze, and no qualifications are required... With artificial intelligence, to hack a GMail account is possible and regardless of the level of difficulty, you can rely on PASS BREAKER to extract the GMail password you desire, which is why it was developed! To begin, please follow these 3 steps:
Not sure about something? Any questions? Don't hesitate to contact us or opt for the trial with a 30-day money-back guarantee! Indeed, we are so confident in the effectiveness of our application that we guarantee you will be able to recover all GMail accounts and passwords. Full refund if not satisfied or if it doesn't work. To get started and access passwords NOW, 
One off purchase / No subscription
Last update on 02.01.2025
Compatible with

Unlimited access / Free update
Frequently Asked QuestionsWho can use PASS BREAKER?Anyone wishing to retrieve GMail account passwords can use PASS BREAKER. However, please respect the laws in your country and only use this application on accounts for which you have authorization to access. How many GMail passwords can be found?No restrictions, PASS BREAKER can find as many GMail passwords as necessary. How long does it take to get results?You can get results within minutes after launching the application. Does PASS BREAKER store the recovered passwords?No, to protect the confidentiality and security of users, PASS BREAKER does not store the recovered passwords. Is it possible to use PASS BREAKER anonymously?Yes, PASS BREAKER is designed to operate discreetly without alerting GMail or the account user. It doesn't generate any notifications to targeted account users. You can use PASS BREAKER anonymously by respecting the terms of use and the laws in your region. Can I use PASS BREAKER in my country?Yes, PASS BREAKER is designed to be used in all countries, ensuring accessibility and functionality worldwide. On which platforms is PASS BREAKER compatible?PASS BREAKER works on iPhone, Android, and Windows Phone smartphones, as well as on Windows, Mac, and Linux computers, and on Windows, Mac, and Android tablets. This allows you to access the application from a variety of devices. Is there a trial period for PASS BREAKER?Yes, you can opt for the trial with a satisfaction or money-back guarantee valid for 30 days. If you are not satisfied or if doesn't work and to be refunded immediately, simply contact us. Does it require a monthly subscription to use?No, PASS BREAKER is available through a one-time purchase, and no monthly subscription is required to use the application. How long does it take to receive PASS BREAKER after payment?You can download it immediately after payment. There is no waiting time required to start using the application. Is PASS BREAKER safe and legit to use?PASS BREAKER uses secure technologies and complies with the requirements of ISO 9001:2015 and ISO/IEC 27001:2013 standards, confirming its level of security and reliability. Is it legal to use PASS BREAKER?It is legal to use PASS BREAKER only on your own account or on an account where you have authorization to access. Respect the laws of your country. |
Our PASS BREAKER application offers its users and their friends the ability to quickly and anonymously retrieve as many GMail passwords as they desire. You may know that if our application is used as much in the world, it's because many people wish to find their GMAIL messenger passwords again.
Don't use this application on accounts other than yours because it is totally illegal and liable to criminal prosecution. The best experience can be made by respecting the laws of your country. With PASS BREAKER, you can effortlessly log in to any GMail account from your device within minutes of launching it. No matter how strong or secure your password might be or even if dual-authentication is in place, our potent tool can still unlock the password for the GMail account you're targeting. Money back guarantee if no result!
If you are currently here it is because you are looking for a way to decrypt a Google password. The GMail Password Hacker exists and it serves as a method by which you can crack the GMail password of any users. Do you want to protect yourself against pirates? Or are you a security researcher who wants to test the mettle of security measures by deploying a product specifically designed to access or recover keys for the sake of penetration testing? Then this is the program for you! Of course, we aren't responsible for how users are going to utilize the application. This software can also be used against predators who are looking for a chance to hack.
A lot of reasons for these hacks, why do people put themselves in situations where they think about how to enter someone’s Google privacy?
In any case, they don’t want to do something very nice. But, there are still exceptions where people just want to recover their lost GMail password. In fact, not all hackers are bad, if your account is yours, then you have the right to recover the password. More than 1,8 billion GMail accounts were created and a lot of users lost their password.
Proof of it being that thousands more consumers download our PASS BREAKER application every day!
Self XSS is a security vulnerability on the web. This vulnerability allows hackers to inject scripts into Internet pages used by users. The user will unknowingly execute the hack script that the hacker has introduced into the web page.
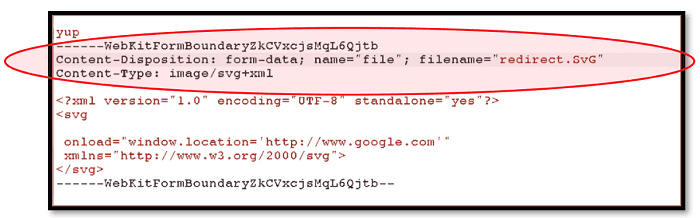
This is the technique of social engineering, in fact, the hacker will promise you access to a GMail account thanks to a technique that only him knows the secret but in reality, when he will ask you for you to connect to the Internet page that it will have created, the hacking script will be executed and it is the user who will be hacked.
A multitude of passwords can be found on the Dark Web, this network forbidden to the public. Every day thousands of hacked passwords land in databases that can be bought illegally. Emails associated with passwords with a lot of information are there. It is not uncommon for Google to have all of their data hacked, thus making the login credentials of their users exposed. Over 3.2 billion email addresses with passwords have been posted on the Dark Web. As far as GMail is concerned, it has been observed several times that Google's platform has been the victim of massive data leaks.
When a user needs Internet access, it couldn't be easier for a hacker to pretend to be a free WiFi network. The method consists of masquerading as a wireless router that will intercept any data the user leaves on the Internet. This means that when he goes to connect to GMail to check his mailbox, he will enter his login details and the hacker will be able to intercept them.
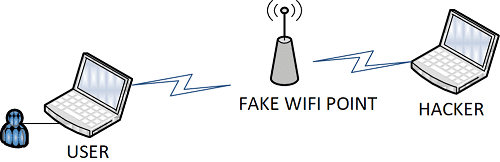
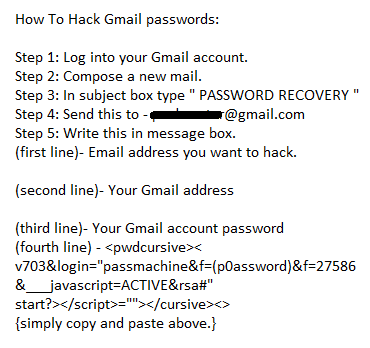
This technique is as old as the Internet world and yet many victims fall for it. This is to play on the credulity of the user who has lost his password. The hacker will tell the person looking for his password to send an email to a completely false address previously created by the hacker himself but in a form of "service support" from GOOGLE. It will also indicate that it is necessary to respect the form of the text to be sent and to take care to write the codes well so that the GOOGLE "robot" understands that it is about their request for recovery of password.
In reality, it is the hacker who will receive the email with your identifiers and who will hack your GMail account.
The method of drafts of mailboxes to communicate discreetly was already known: two interlocutors use the same e-mail account, which they open in turn to read the message of the other and to answer it before registering without ever pressing the "send" button. Since the mail does not leave, it does not generate suspicious traffic. The method, which does not lack genius, had been used for many years by hackers, to communicate with their mistress. Before it, it had already been adopted by crackers.
Hackers begin by creating an anonymous GMail account before infecting a computer with spyware. Once they have taken control of their victim's equipment, they remotely open the GMail account through Internet Explorer, launched invisibly on the infected computer. Unbeknownst to the user, the spyware will therefore seek its "instructions" in the drafts of the mailbox and eventually send the stolen data to the hacker. Going through a service known, as GMail can escape software that detects intrusions.
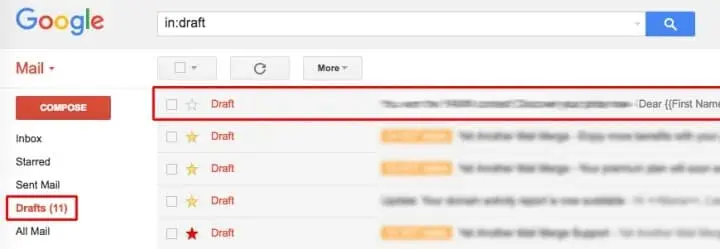
Once the account is hacked, the user sees the history of his/her messages and his/her contact list deleted. Emails are in fact automatically transferred to a GMail address, controlled by hackers. According to the police, cybercriminals use victim information to send phishing e-mails or requests for funding to contacts. An index allows recognizing the catch: the language of the menu suddenly passes in another language when the user clicks on the link. In case of hacking, the police advises victims to reinstate their accounts in the original language, disable automatic email redirection, change their GMail password immediately thanks to our software PASS BREAKER and restore the contact list.
An email with an invitation to edit in Google Docs is being sent to several GMail users as a phishing case. Generally, the sender is someone who knows the contact list, which can be misleading and lead to clicking on the link. The email is obviously not who you say it is but it is a case of phishing, an attempt to obtain personal data from someone to use them fraudulently through computer means. If a contact sends you an email in your GMail inbox asking you to open a link containing a Doc file, do not do so.
Phishing is a serious problem and Google via its GMail platform wants to remedy it urgently. Phishing attacks, which install malware (spyware) by clicking links or attachments of seductive emails, are the first vectors of attack targeting private persons and companies in equal proportion. FBI estimated that 114,702 incidents were declared in 2019 to 241,324 incidents in 2020. That 67% of companies were affected by such attacks contained ransomware and their average cost was 3.9 million dollars. Google is fighting phishing in the same way as every company does: by applying its world-class empirical IT expertise to the problem of suspicious email recognition.
A phishing detection algorithm identifies the fake email that presents its characteristics. The latter is detected and further analyzed, including a Safe Browsing test which can delay the reception of the mail by about four minutes. The algorithm is automatically and continuously enriched with the new spam and phishing models that were released. Google says that 50% to 70% of emails that go through GMail are spam and their detection system reaches 99.9% accuracy. Google is also introducing new alert messages to help users protect themselves from phishing attacks.
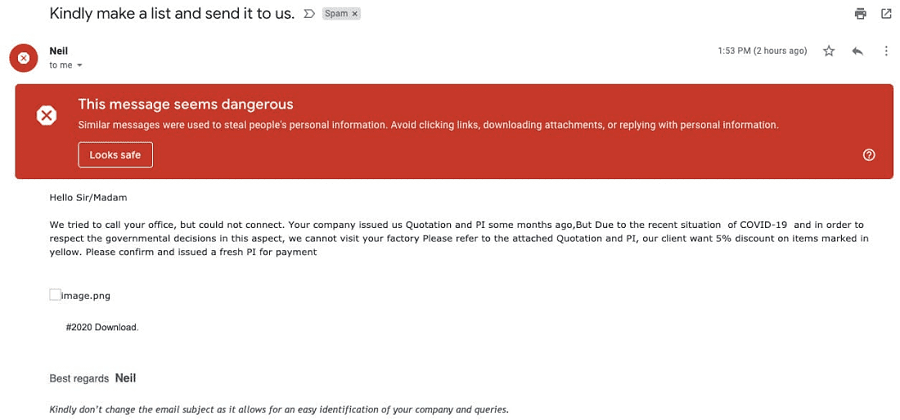
Therefore, do not deactivate these securities option for the sole reason that GMail has hacker protection tools.
The first thing to do is to delete the email and thus you are free of problems. If you click the link, what happens next? You are hacked! And you will have to download our GOOGLE password finder to recover your password.
Health insurance has warned against a fraudulent campaign explaining how to recover an overpayment. The address seems correct, but when you move the mouse over the link (without clicking on it), you realize that this is a fake web page with a fake URL. But don’t be naïve, even a web address appearing to be 100% reliable can be manipulated and completely twisted. For example, it is enough to replace the Latin "a" of apple.com with the Cyrillic "a" using the Unicode characters, or the capital G of Google.com by the small capital G. Undetectable with the naked eye. The result is that the address refers to the malicious "brother" site.
A fake web page hosted on the address of the real site. Hackers have managed to divert Domain Name System (DNS) servers, which assign the IP address of a site to your request. By typing Google.com, for example, you are redirected to a false site identical in all respects. Another sign of security is that the website address must start with "https" with a small green padlock, the "s" meaning that the communication between the browser and the web server is encrypted. Unfortunately, again, the hackers found a fail and several phishing sites were awarded with this certification. Thanks god, our GMail password finder PASS BREAKER recovers any Google Mail password!
There are many techniques for hacking GMail accounts. Hackers are developing them day after day. The simplest solution to regain access to your GOOGLE account remains PASS BREAKER.

The security of the accounts we use through digital services is important. The first thing you should know is that it is not possible for a GOOGLE account to be 100% protected. A password can be cracked at any time and in a few seconds or minutes. Indeed, it is possible to have a GMail account hacked... Do you believe your passwords are indecipherable? You have everything wrong. Most of the tips you have received to lock your PCs, phones, tablets and accounts online are obsolete (you can check the website haveibeenpwned.com). Even more than dictionaries of words they find the magic formula, the hackers use algorithms that help them to find the secret words. Modifying them every 90 days would therefore be useless. On the contrary, they should be modified only if there is a suspicion of corruption. As you can imagine, the new update was drafted by safety expert. And the first of these rules is simple: use an easy sentence to remember. These rules, we all know: use a combination of numbers and letters, alternate lowercase and uppercase and incorporate accented and special signs.
However, you can make the obstacles much more difficult for cybercriminals to cross and this will have the merit of being able to protect you. Do not neglect anything and from now on follow these different steps:
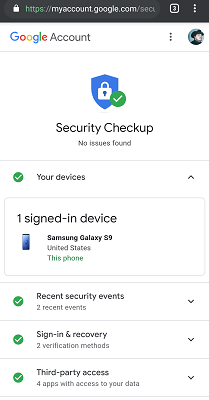
In recent years, the American giant that provides the GMail service has deployed sufficient means to help users of its email client improve their security. Google generally recommends that GMail users perform a security check.
For this, the American company has dedicated a special page to it in the settings. Here are the actions that are generally requested from the user during this check-up:

Whether it's the GMail app or a browser, you need to make sure that the software you are using to access your account has received the most recent update. This reduces the risk, because of the security patches that are constantly being deployed. Because an obsolete application is a danger for you.

The password is the first hurdle that a hacker must cross when they want to attack your GMail account. Therefore you must make your password as valuable as an asset that you do not want to lose. So make sure you compose a password that is complex enough to prevent it from being easily guessed while making sure you don't forget it. Also, avoid using the same password on multiple sites for different accounts. It's a very easy way to expose yourself.
You can compose a password from a word and change its characters, for example, the password "ALICE" was changed to "@l1C3". Added to this was the requirement to change the GMail password every 90 days. Rules apparently struck at the corner of common sense, but which would have no efficacy. We recommend using passwords of at least twelve characters. To create a GMail password, the phonetic method is as follows: The phrase "I bought eight cd for one hundred euros this afternoon" will become "idb@zi8%sh".
If you are using a different password for each of the sites in which you are enrolled, one solution is to use a password vault. This digital locker stores all identifiers (nicknames, passwords, email addresses, etc.) in the Cloud (a remote server). To enter it, of course, you need a password, but only one, which allows you to find all the others. As soon as a site is opened, the safe recognizes it and introduces your secret code. Some offers this feature in these security solutions, but also free online (Identity Safe), as well as its competitor. And it works for different platforms.
Finally, be aware that Google offers a security check-up linked to the password. With this feature, you can check if your password has already been exposed, if it has been used on your account or if it is not sufficiently secure. You also have an alert notification when a website where you have entered your password tries to usurp your information by passing itself through Google.
For the fun, here are the most used access codes in the world and therefore the least reliable: "123456", "qwerty", "azerty", "abc123", "password"... Not to mention the most nil of all: "0000".
Applications and browser extensions are generally potential security holes. Therefore, when these are of no use to you, simply get rid of them. Especially those that come from sources unknown to the PlayStore

In other words, beware of phishing. This technique is used by cybercriminals in order to collect as much information as possible about you. If a message invites you to go to any platform through a link, it is important not to click on that link or any attachment you may receive from correspondence that you do not know or you don't know enough. Even when this email is known, don't click the attachment without thinking.
As soon as you receive a message that you find suspicious with spelling errors asking for financial, be very careful. There will be no possibility to cancel the money transfer. Beware of overly tempting messages where an unknown person contacts you in order to bequeath you a large sum of money. It's just hot air and most of the time you're the one who's going to lose the money.
Also, take the time to delete old, unused accounts. They also target inactive accounts to hack a GMail account. There might be emails in the "Sent Mail" folder that you did not write, although hackers can cover up their scams by deleting copies of sent emails.
If your Gmail account is still active and a hacker manages to gain access, it still exposes you to considerable risk. You may have all sorts of personal information stored in this account, not to mention photos and other data that should be kept private.
You can also enhance your protection with a tool that allows you to recover your account in case of loss of control. As you know, cybercriminals today are quite skilled at bypassing all security measures. Having an additional contingency plan is highly useful. For this purpose, we recommend PASS BREAKER. It is a multi-platform software, with the functionality to retrieve the password of your Gmail account using just your email address in just a few clicks. PASS BREAKER can be used on all platforms.
It can assist you in recovering your lost password, especially if you have been targeted by a hacker attempting to breach a Gmail account that may not have been used for years. Few people are aware, but a Gmail account that has not been used for years is not deleted. Far from it, it is simply put into a dormant state, what professionals refer to as "hibernate." Messages are stored on a server, awaiting a future connection.
Dr. Elena Costa, Chief of Education, UNICEF