PASS REVELATOR is the application that allows users to discover all passwords of MSN, Hotmail or Outlook (including all Office 365, live.com accounts, etc.) by efficiently breaking and decrypting them using artificial intelligence.
Imagine that at any time and without limitations, our tool can recover any password worldwide.
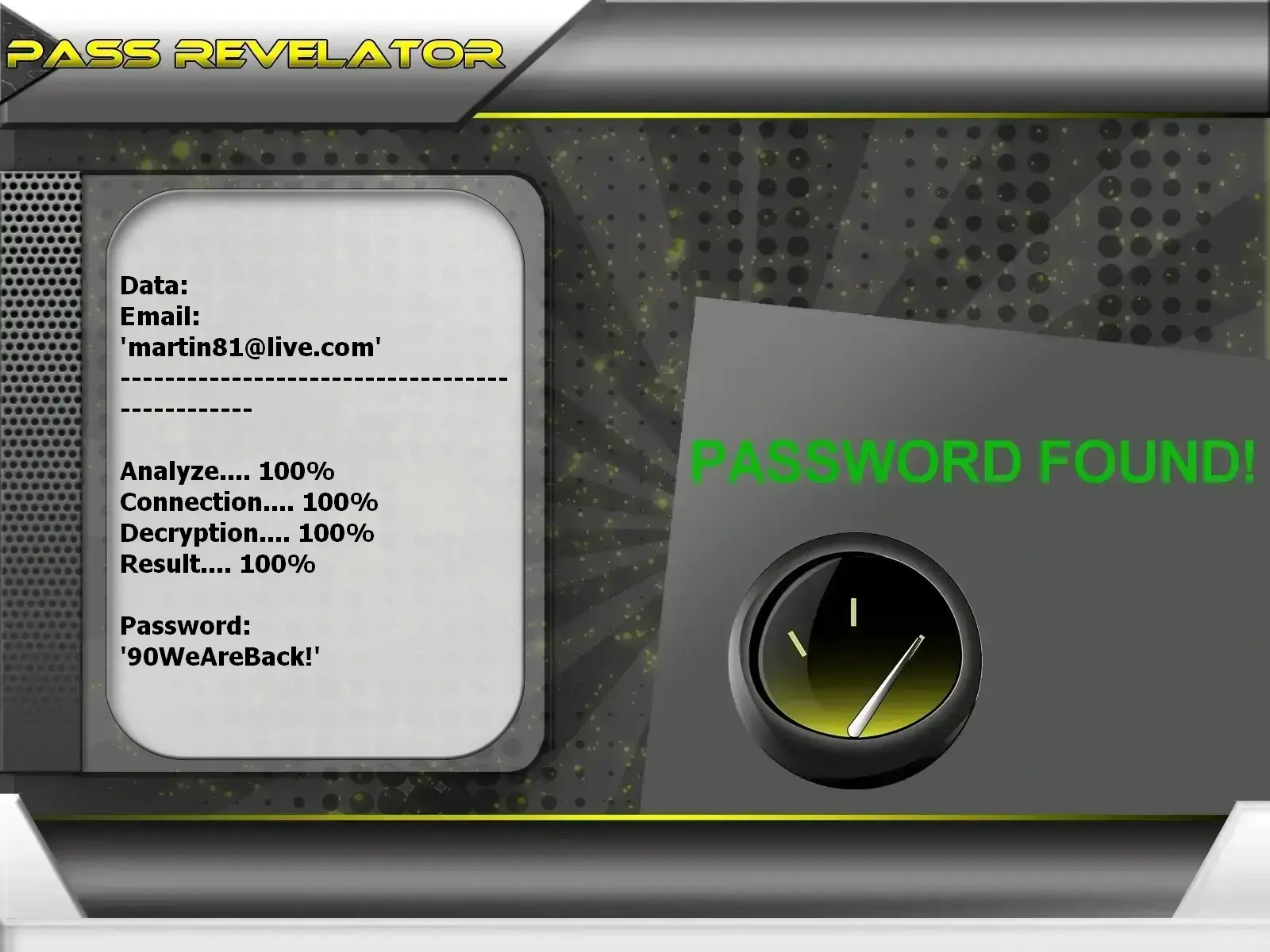
Try this simple hack and be amazed by the results! PASS REVELATOR provides the current MSN, Hotmail and Outlook passwords associated with that account.
You can recover your forgotten password as well as the passwords of your friends!
PASS REVELATOR employs artificial intelligence to capture encrypted data, facilitating quick password hacking for targeted Outlook accounts.
PASS REVELATOR simplifies the cracking procedure by integrating an advanced AI-based algorithm. A powerful system is integrated for real-time data interception and analysis, coupled with a sophisticated script-based process for cryptographic decryption. Once the password is identified, the next step is to process it using a neural network to achieve precise and efficient results. This allows the password to be displayed in plain text on your screen in just a few minutes.
The advanced capabilities of PASS REVELATOR also enable it to bypass two-factor authentication (2FA) protections. Additionally, no notifications will be triggered during the login process, ensuring complete discretion.
![]() WARNING: You must
not use the application to log into an account that doesn't belong to you. Read the rules, be aware.
WARNING: You must
not use the application to log into an account that doesn't belong to you. Read the rules, be aware.





GIVE IT A TRY NOW!You don't need experience to get started... Thanks to artificial intelligence, to hack a MSN, Outlook (also all Office 365, live.com) and Hotmail password is possible and PASS REVELATOR decodes accounts without any restrictions, that's why it was developed! To begin using PASS REVELATOR, kindly proceed with the following 3 steps:
Not sure about something? Any questions? Don't hesitate to contact us or opt for the trial with a 30-day money-back guarantee! Indeed, we are so confident in the effectiveness of our application that we guarantee you will be able to recover all MSN, Hotmail and Outlook (also all Office 365, live) accounts and passwords. Full refund if not satisfied or if it doesn't work. To get started and access passwords NOW, 
One off purchase / No subscription
Compatible with

Unlimited access
ISO 9001:2015 & ISO/IEC 27001:2013 certified
Frequently Asked QuestionsWho can use PASS REVELATOR?Anyone looking to retrieve passwords for Outlook (Office 365), Hotmail, MSN, and Live accounts can use PASS REVELATOR. However, please make sure to only use this application on accounts you have permission to access. How many Outlook passwords can be found?PASS REVELATOR can find an unlimited number of Outlook passwords. How long does it take to get results with PASS REVELATOR?With PASS REVELATOR, results are obtained in just a few minutes. Once you launch the application and provide the required information, it automatically decrypts the passwords for Outlook (Office 365), Hotmail, MSN, and Live accounts. Is the security of retrieved passwords guaranteed by PASS REVELATOR?Absolutely, PASS REVELATOR ensures the total security of retrieved passwords. No data is stored to preserve the integrity and confidentiality of users. Is usage of PASS REVELATOR anonymous?Yes, PASS REVELATOR operates discreetly to avoid alerting Outlook or the targeted user. It generates no notifications, ensuring anonymous usage, though it's important to adhere to relevant regulations. Does PASS REVELATOR work in all countries?Yes, PASS REVELATOR is designed to work globally, catering to users in various countries and regions. On which platforms is PASS REVELATOR compatible?PASS REVELATOR works on iPhone, Android, and Windows Phone smartphones, as well as Windows, Mac, and Linux computers, and Windows, Mac, and Android tablets. This allows access to the application from a variety of devices. Is there a trial period for PASS REVELATOR?Yes, there is a trial period for PASS REVELATOR. We offer a satisfaction or money-back guarantee valid for 30 days after purchase. If you are not satisfied with the results or if it doesn't work, you can request a refund by contacting us. Does it require a monthly subscription to use?No, PASS REVELATOR is available for a one-time purchase. There is no monthly subscription required. Once you've purchased the application, you have unlimited access to its features. How long does it take to receive it after payment?You can immediately download PASS REVELATOR after making the payment. There's no waiting time to start using the application. Is PASS REVELATOR safe and legit to use?Yes, PASS REVELATOR is an application certified compliant with ISO 9001:2015 and ISO/IEC 27001:2013 standards. This ensures its security and reliability when used to retrieve passwords for Outlook (Office 365), Hotmail, MSN, and Live accounts. Is it legal to use PASS REVELATOR?The legality of using PASS REVELATOR depends on your intentions and the legality in your jurisdiction. It is recommended to only use this application on your own accounts or with explicit permission from the owner of the targeted account. |
PASS REVELATOR is the application that allows you to extract passwords for Outlook (Office 365), Hotmail, MSN and Live accounts. Regain access to your account and emails in just a few minutes. Be careful not to download a software that is intended to encourage you to try by any means to hack, crack MSN password or steal the pin code of a Hotmail account of your friends or people you know.
Don't waste another second! Start your PASS REVELATOR trial to easily and quickly decrypt the passwords for each account! After that, you'll be able to log in successfully. If not, money back guarantee!
Only very few people take piracy seriously and the result is that our PASS REVELATOR software is downloaded hundreds of thousands of times per month to help users recover their or others passwords.
It has more than 600 million active users, a boon for hackers to crack Outlook, MSN or Hotmail passwords.
For more than 20 years, hackers have been trying by any means to grab the Outlook accounts with linux servers, keyloggers, phishing pages... for several reasons:
Still forgetting passwords? Who has never lost his email password at least once in his life? Or even got a Hotmail account hacked? The best solution yet to help you is PASS REVELATOR. It can be very insecure to no longer have access to your email. Your data can be in danger and lost forever!
It is possible to obtain any hacked database information. All that is needed is to know the ID of a victim. There are many ways to hack Outlook password but it is not as easy as you might think. To do this trick you should at least have knowledge in programming.
Here are some of the most common hacking techniques:

The sign "Peace" is a great classic for selfies, a unifying gesture that is regularly found on social networks. However, when you read the following article, you will probably think twice before showing your fingers on your next selfie and for good reason since depending on the quality of the photo and the distance from which it was taken, the hackers are now able to steal your fingerprints.
According to computer scientists, it is possible to reproduce a person's fingerprints using a photo posted on the Internet. Getting fingerprints from a selfie? This is possible, hackers can recover the fingerprints thanks to the photos posted on the social networks. The quality of cameras needs to be at least the one of a smartphone to make this possible to a hacker, it is first of all thanks to the camera sensors, which offer a very high precision, up to twelve million pixels. This sharpness makes it possible to zoom in on the fingers, often in a V-shape, less than one meter from the lens. But the experts also managed to hack fingerprints during a test when the photo was taken at a distance of three meters!
We can recover pictures from Microsoft OneDrive from which we can, with some work, reproduce a fingerprint. They also hacked the fingerprint of a minister! Especially since this is not the first time that hackers have fun with this manipulation. Some years ago, at a conference, a hacker took a picture of a German minister while he was speaking, he had reproduced his fingerprints and managed to unlock his cell phone. Since fingerprints can be stolen, copied and used to bypass today's login, it is clear that passwords can still offer their services for years and years.

Hackers use the trusted friend feature of the email box to steal the credentials of many accounts. A new phishing campaign is raging on Hotmail. It uses the trusted friend function.
Phishing is a technique that consists in making the user click on a link, in order to retrieve all his identifiers. The method is simple and always the same: hackers pretend to be one of your friends, already infected, to spread a fraudulent virus. The friend in question tells you that his account is blocked. The trusted friends feature allows you to contact three to five friends in case of a connection problem. A link is sent to unlock the account. The link would have been sent to you in an email. You open the email and all your credentials are retrieved by the hacker. In fact, the code to recover its credentials must be sent in individual parts by all trusted friends, not just one as alleged in the MSN message by hackers.

It is a practice that doesn't require having very skilled knowledge in hacking. However, it demands to know how to use social relationships to extract as much information as possible from your target. More often than not, hackers practice social engineering through social media. They can do this directly or through a group process.
Direct social engineering will consist in creating a friendly or emotional bond against a particular person. It can also consists in exploiting the relation that already exists. How ? Quite simply by pushing the individual to provide personal information. This information is then processed by the hacker to deduce connection identifiers.
Social engineering in an indirect way will consist in initiating a group conversation under a publication. Most often these exchanges relate to subjects which seem banal but which are really targeted by the hacker. Usually these are questions like: what's your dog's name? What was your favorite color as a kid? What's your birthday? Questions that are most often our security questions that are likely to constitute passwords.

More often than not, our communications are not really secure because we have become accustomed to believing that we are not important enough to be targeted by hackers. However, all Internet users are in some way important to hackers. Your computer data is so precious that they are always developing new attacks to hack you. The man-in-the-middle attack will simply consist of intercepting your communication by serving as a relay between you and the server with which you want to communicate. Several methods can exist for this. But there is one that seems easier and simpler: the deployment of fake WiFi hotspots. In this tactic, the hacker creates a fake free WiFi hotspot. When this fake WiFi hotspot is available and the Internet user accidentally connects to it, it is possible for the hacker to intercept the user's connection. This gives him the advantage of collecting the connection data he needs to succeed in its hacking.

On the Dark Web there are huge databases that contain a lot of login information. This information is often the result of data breaches or large-scale hacks carried out by very knowledgeable hackers. If you know how to manage a database and find information that interests you in particular, this technique may be right for you.
It is surprisingly easy for crooks to see poor user protection. Even a similar account can give scammers access to personal information like your username, real name and even your location! Now that you are armed with a little more knowledge about the cyber scam, post your selfies with confidence. Especially if you no longer have your password, quickly install our PASS REVELATOR tool!
Very often to get your Outlook box hacked, it only needs a simple moment of inattention or an unfortunate little click on a spamtrap email or an unsecured connection on a public WiFi network or as we told you above, the malice of a close friend. A good password does not do everything, but there is no reason for not putting a strong enough one! Typically, a password consists of letters, numbers and special characters. But this is not going to prevent hackers from hacking your email account. Nothing is foolproof in IT.
The worst thing about it, is that the man responsible for all these daily nuisances regrets today to have established these rules. It includes the following tips: use special characters, uppercase letters, numbers. But also ask a new password to the user regularly. Recommendations that follow the same logic: prevent hackers from successfully guessing the password using programs that test all possible combinations. The more characters possible, the longer it takes for a machine to test all possibilities (Learn how to create super-strong passwords).
These recommendations had a perverse effect. Faced with the complexity of these strange passwords, difficult to memorize and to change regularly, many people have cheated. For example, simply put a capital letter at the beginning or a number at the end. This will be sufficient in order to succeed in hacking a relatively short password quite easily. This is what they illustrate perfectly: a short password, composed of four words without any link between them, is easier to remember for a man and more difficult to break for a machine.
In the end, it was probably too complicated for many people to understand these recommendations, we were wrong. In the latest edition, published recently, the network companies advise to stop asking users to change their password regularly. Similarly, users should no longer be forced to add special characters in passwords. This will make it possible to create a longer secret code, yet easier to remember.

You need to know this, Microsoft is not going to ask you in an email to give your password. In other words, these kinds of emails are usually initiated for the purpose of phishing. Therefore you must be vigilant.

Keeping your devices and software up-to-date is essential to ensure better security. Most of the time the users tend to delay these updates or even are going to neglect them. This is a mistake you must not make. As soon as you see a notification about an update, go ahead and deploy it.

This is also the least you can do. No security procedure will be effective if you don't have a secure device to start with. Therefore, be sure to use smartphones or computers that meet the highest security standards possible in your situation. Do not hesitate to install security updates of the operating systems of these devices. Install security software to increase their protection. In addition, avoid installing applications from unknown sources on your devices. When you are not using a particular application, simply erase it. In addition, grant the minimum authorization to the various applications that are functional on your terminals.

It is essential to verify how things are going through your account. Don't just open it when you are expecting an email or when you only have a notification. Go there every now and then to see if there is anything unusual. In addition, Microsoft will take care of warning you insofar as there have been actions or connections that are outside of the framework of your habits.
It’s an identification measure strongly recommended regardless of the platform. With Outlook you have the possibility of opting for two-factor authentication by sending an auto-generated code, or a connection using Microsoft Authenticator. Obviously this represents redoubled security and protects you as much as possible against phishing.
You will need to be disciplined and put in place all the measures we mentioned above. PASS REVELATOR will allow you to no longer be anxious when you have for example lost your password or if you are in a situation where your account has been hijacked. It is a cross-platform computer program, which can be used on devices running on all systems. It lets you find your account password in just a few minutes, just with the email address or phone number associated with the account. Therefore do not hesitate and use it!
Abdalla Al Ali, Chief Police Officer, Dubai Police Force