PASS WIFI is the legitimate and certified application, compliant with ISO 9001:2015 and ISO/IEC 27001:2013 providing free access to all wireless communication protocols through the power of artificial intelligence benefiting a comprehensive and sophisticated analysis of network connections.
This process is carried out effortlessly, with unlimited use and no time restrictions.
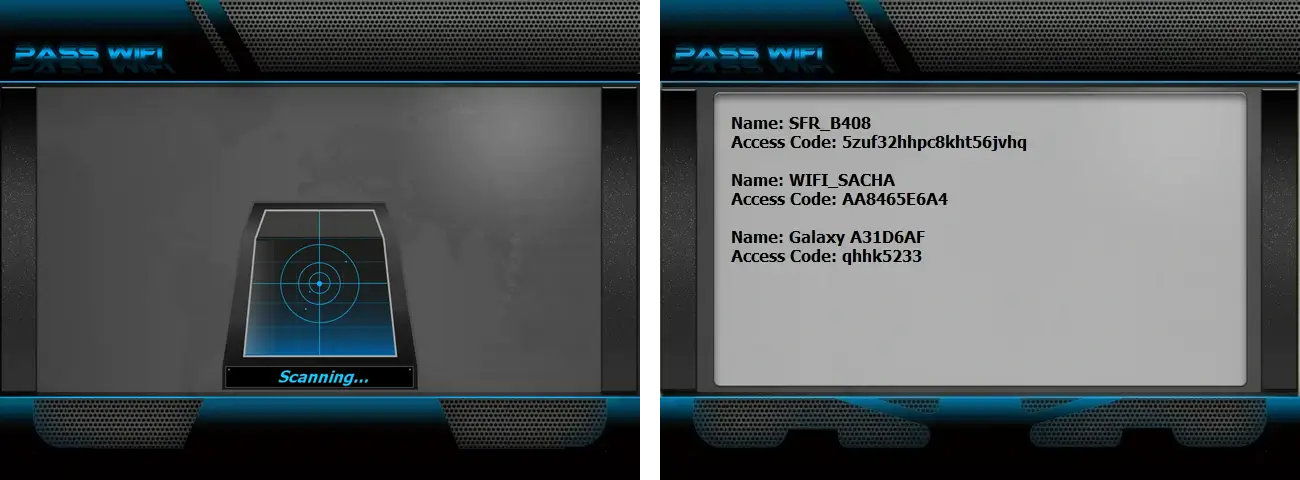
Try this simple hack and be amazed by PASS WIFI's results! There's no need to be a computer expert to access the Internet. It scans and retrieves all keys of secured connections.
PASS WIFI is capable of reading and decoding various types of protocols such as WEP, WPA, WPS, WPA2, WPA3, EAP, 802.1X, RADIUS, TKIP and AES. You can quickly connect to any WiFi network from any provider because it scans and retrieves all secure connection keys from the routers directly. It is fully compatible with all of these protocols!
By directly exploiting vulnerabilities in router databases, PASS WIFI will automatically execute a complex and optimized asymmetric cryptographic decoding algorithm to extract all detected WiFi passwords within minutes from any location.
![]() WARNING: Don't use this application to access networks you don't have permission to connect. Read the rules, be aware.
WARNING: Don't use this application to access networks you don't have permission to connect. Read the rules, be aware.




GIVE IT A TRY NOW!It’s a piece of cake and no qualifications are necessary to get going... By exploiting artificial intelligence, to hack a WiFi password is possible as explained above and you can decrypt as many WiFi passwords as you want, this is why PASS WIFI was developed! Kindly proceed with these 3 steps to begin using PASS WIFI:
No sure about something? Any questions? Don't hesitate to contact us or opt for the trial with a 30-day money-back guarantee! We're exceptionally confident in the effectiveness of our application, so we assure access to all WiFi passwords. If you're not satisfied or the application doesn't meet your expectations, you're entitled to a full refund To get started and access passwords NOW, 
One off purchase / No subscription
Last update on 01.01.2025
Compatible with

Unlimited access / Free update
Frequently Asked QuestionsWho can use PASS WIFI?PASS WIFI can be used by anyone wishing to access WiFi networks for which they have permission to access. How many WiFi passwords can be found?PASS WIFI has no usage limit and can find as many WiFi passwords as needed. How long does it take to get results with PASS WIFI?Results with PASS WIFI are obtained within minutes after launching the application. Is the privacy of retrieved passwords guaranteed with PASS WIFI?Absolutely, PASS WIFI ensures complete protection of retrieved passwords. No information is stored to preserve the security and integrity of users. Is PASS WIFI usage anonymous?Yes, PASS WIFI operates discreetly to avoid raising suspicions. It allows anonymous usage, but please ensure strict compliance with regulations in force. Is PASS WIFI supported in my country?Absolutely, WiFi-emitting routers adhere to the standardized IEEE 802.11 norms, widely utilized across the globe. PASS WIFI is specifically designed to ensure universal compatibility, thereby granting users from various countries access to its features. On which platforms is PASS WIFI compatible?PASS WIFI works on iPhone, Android and Windows Phone smartphones, as well as Windows, Mac, and Linux computers, and Windows, Mac, and Android tablets. This allows access to the application from a variety of devices. Is there a trial period for PASS WIFI?Yes, PASS WIFI offers a 30-day trial period. If you are not completely satisfied at the end of this period or if it doesn't work, you are entitled to a full and immediate refund simply by contacting us. Does it require a monthly subscription to use?No, PASS WIFI doesn't require a monthly subscription to use it. It is a one-time purchase. How long does it take to receive PASS WIFI after payment?Download is immediate after payment, there is no waiting period. Is PASS WIFI safe and legit to use?Yes, PASS WIFI is safe to use. It is certified compliant with ISO 9001:2015 and ISO/IEC 27001:2013 standards. Is it legal to use PASS WIFI?The legality of using PASS WIFI depends on your location and how you use it. Always respect local laws and regulations regarding WiFi network access. |
With PASS WIFI, you can obtain network PIN codes from your neighbors or friends in just a few minutes after running the application. Don't use PASS WIFI on other WiFi than yours because it is totally illegal and liable to criminal prosecution. The best experience can be made by respecting the laws of your country.
Since the introduction of WiFi, a radio telecommunication technology in 1990, many have desired to have free access to the Internet worldwide. A WiFi network is never 100% secure, as one might believe; there will always be vulnerabilities. Consider that hacking a wireless network is genuinely possible!
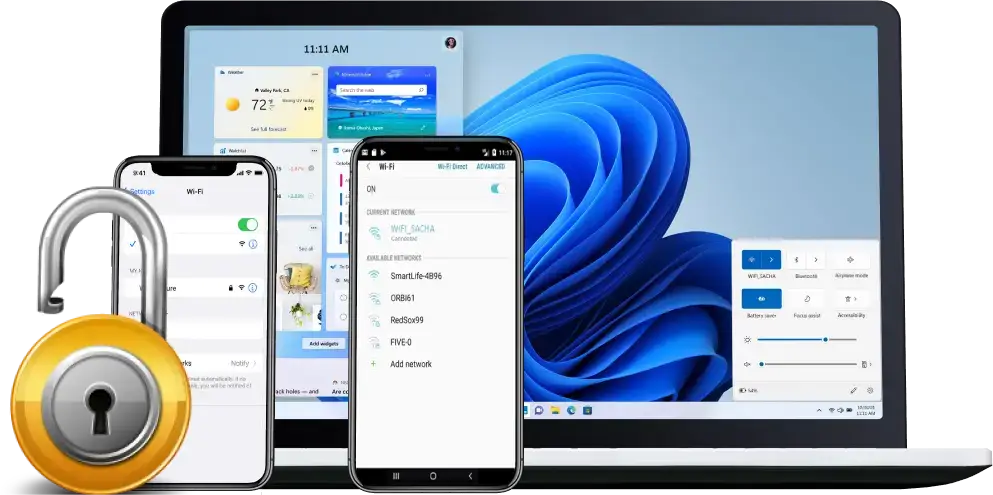
With the PASS WIFI application, you can now retrieve the connection keys for networks, whether it's from your neighbors, family or friends, just minutes after launching the application. If in the following few minutes you are not connected to a wireless network thanks to PASS WIFI, the refund guarantee will apply.
In reality, there are several reasons for hackers to use wireless technologies:
A hacker will not crack WiFi codes for nothing. Now we are not talking about white hats but we are talking about black hats, those who hack into WiFi connections for bad intentions.
Indeed, these hackers will interfere with the privacy of Internet users and they will retrieve all information and personal data. For example credit cards, files going in and going out, emails... Users connected on the network will not notice anything! But you have to know that this could also be done from a smartphone. It is possible to hack a WiFi with a mobile working on Android, iOS (iPhone) or a Windows Phone.
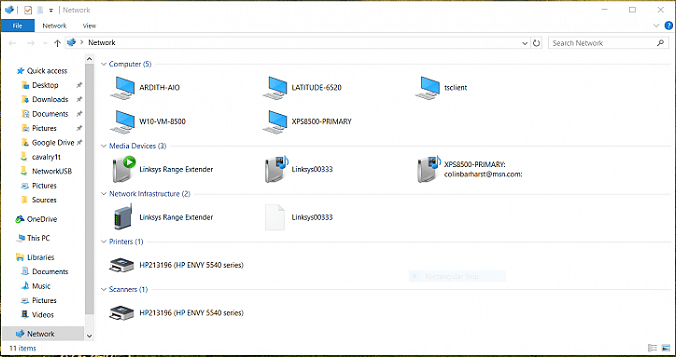
You can check yourself from your computer in your network properties if a third party is logged in. That would mean that you are hacked. This could be dangerous if you selected the way you share your printer or your files. Everyone can have access to it and dissimulate a virus in it. What you should do is to install a good antivirus, run an update and run a deep scan. Then you should install a firewall if it is not already given with the antivirus you previously installed.
After that, you should rename your router and change the password. This step could be a little complicated, but generally the user manual indicates the steps to do this task. For the password, you should take WPA protection which is 99% good. Keep in mind that not every password is 100% secured and can be hacked any time.
A security flaw was discovered that allows for the hacking of the WPA protocol. This vulnerability enables the hacking of the PSK shared WiFi key, thus granting access to a wireless network. It's not necessary to capture a complete 4-Way Handshake; the hacking focuses on the RSN IE, which is a part of robust security network information.
The hacker is now in direct communication with the WiFi terminal, eliminating the need to capture the bits a user receives to connect to a network. This means that anyone can directly access a WiFi network at any time, as they can see the password displayed in clear text on their machine. Most routers are susceptible to this flaw, as it pertains to 802.11 networks.
WiFi Protected Access (WPA) and WiFi Protected Access II (WPA2) are two security protocols and security certification programs developed by the WiFi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses that researchers had found in the previous system, WEP (Wired Equivalent Privacy).
Very often in the network options is written "private WiFi network", that is password protected, but now WiFi password crack has become simple and an easily-solved problem. PASS WIFI displays in real time the password of each router. It is clearly impossible to protect a wireless network unless you change the key every minute.
Below are some other methods to hack WiFi passwords (only for computer specialist):
The meaning of WiFi Sniffer is
quite
simple. It is the way for a computer to search for wireless network without any protection
and to
hack access to it for free! WiFi sniffing tools can help you locate open networks that may
not be
visible and will let you know when it is accessible or not for your device. It could be
dangerous
for your network to have an unauthorized person connected because who knows for what purpose
he is
on it?
It scans for available wireless networks within your range, it contacts them, after the contact is established, it receives packets. After the packets are received, it decrypts them, meaning it gets the password with the application tool. Some wireless networks can be opened in a few moments, some can take a few minutes. This depends on how the wifi password is made.

There are still too many people on the earth that don’t have access to the web. With FREE WiFi access point, you can watch your favorite show on holiday. You can occupy your children in the traffic jams. You do not have a TV at home but want to watch a program? If you have a smartphone with internet connection, it is possible to watch some channels for free. Being able to watch TV on your smartphone can be very convenient in many situations.
With "Find WiFi", Facebook now helps us find an Internet connection everywhere! This system should allow us to easily spot the hotspots close to our position. Facebook has begun deploying a new feature that locates WiFi networks nearby. It allows users in areas not covered by 3G-4G-5G networks and those who wish to save data to access a WiFi map of access points located in the area where they are.
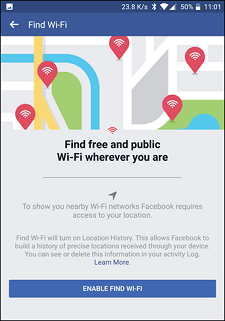
Already accessible under iOS and Android, the map will not only reveal WiFi networks open and accessible to everyone. Those companies that have shared information with Facebook will also be displayed. Finding a network should therefore become fairly simple, provided it is in an area well-provided with access points.
To start the search, you will need to have downloaded the latest version of the Facebook application and go to the menu indicated by three small horizontal bars the "Find WiFi" button. The application should also be allowed to access our location. Once the map is loaded, connection points then appear around you. This new feature has a slight flaw: a little bit of network connection will be needed to load the map showing the access points. No problem when you just want to save your precious data, but if the network is too weak, it will take a bit more time.The representatives nevertheless explained that "Find WiFi" even worked in places with a weak network.
Tests showed that the feature was particularly useful in areas with little mobile network, a way to find a more powerful wlan connection. This service is a new step forward for Facebook in their search to connect the world to the Internet. After all, if the social network really needs to bring people together, it's better for all to have access to a common digital space.

Many of us use their hotel's WiFi to connect to the Internet. The opportunity to remind people that it is necessary to be extra vigilant because these networks are often the target of hackers and this whatever the standing of the hotel in question.
Hackers use a new Trojan attack called Inexsmar. It is downloaded automatically after opening a file attached to a phishing mail. The mail is very credible and targets high personalities thanks to social engineering: the victim, despite his vigilance, is likely to fall for this. In addition, the malware is downloaded several times so that it is not detected by antivirus. If this campaign revealed that it is apparently only about politicians and that the group is known for targeting businessmen in luxury hotels, the warning can only remind us that WiFi networks are a privileged target for hackers. Critical vulnerabilities can be exploited to spread malware and spyware on computers and smartphones connected to the targeted network.
An attack facilitated by the fact that the routers of hotels are sometimes not up to date in terms of security. Users should therefore be extremely careful when using them, of course, have their own antivirus software up to date and configured with the highest level of security.

Sidejacking, also known as session hijacking, is a WiFi attack where attackers use your cookies to impersonate your account and log into any website. They have access to your online accounts and can hack all of your accounts.

A technique more and more used is the Social Engineering which consists in hampering the usual protection systems. Although websites do encrypt your login process, they never encrypt your cookies which leaves your accounts vulnerable. Via the airwaves, an unprotected WiFi network shares session packets making your home or work network much more vulnerable with a high probability of being attacked. These techniques include phishing attacks and scareware attacks.

Unlike the first technique we mentioned above, the man-in-the-middle attack requires you to have a good mastery of hacking because it will push you to deploy enough knowledge and technicality. In this context, how do hackers do it? Most often they create a fake WiFi hotspot identical to that of the targeted user. Once the latter connects to the fake WiFi hotspot, believing it to be the real one, it will enter the password for the real WiFi network. The hacker quite simply recovers this information which has been freely entered by the victim.

Password cracking will consist of the hacker trying to guess the password using several methods. It is a very common practice on the web. He can use the random test method which will consist of composing passwords according to a criterion customary for users of digital services. Such as the use of birthdays or social and family references. The hacker can also proceed to the use of a dictionary, which is in the context a text file which gathers thousands or even hundreds of thousands of already predefined passwords. It is a method that takes a lot of time and the effectiveness of which is not always certain. In addition, the hacker can proceed by the brute force attack. A method which uses software with automated operation which is able to test several types of combinations of characters, numbers, letters in order to find after a certain time the real password. However, this method requires very good mastery.

The Trojan horse is a very popular malware in the hacking community. It is notably one of the most persistent threats that can target a digital service user. As the name suggests, it is a type of malware that usually takes the form of a legitimate computer program. It can in particular hide behind another program and activate when the latter is already installed on the targeted terminal. When a Trojan horse is installed on a computing device, it can provide several types of functionality. Indeed, the hacker can spy on his victim using software. It can take control of the infected computing device and make it perform tasks remotely. In particular, it can be used to collect data such as passwords and other identifiers.
You will need the right tools and resources to stay safe and protect those around you in the event of a cyber hacking into the WiFi network. The Internet now touches almost every aspect of our daily life. Our PASS WIFI tool allows free access to the Internet without worrying about these issues.
We are able to shop, connect on social media, connect with family and friends and manage our medical records online. These activities require you to provide sensitive personal information such as our name, account numbers, addresses, email addresses, passwords and location information. All of this can quickly turn out to be dramatic if someone has hacked into the WiFi network.
PASS WIFI works on all small devices and allows you to test network security. Within seconds or minutes, it displays WiFi status and passwords. Our PASS WIFI tool allows free access to the Internet without worrying about these problems.

You have a WiFi hotspot for your internet connection requirements. You know that it is important to secure it to prevent other people from taking advantage of it without your knowledge.
Securing your WiFi has several advantages:
 It allows to minimize the bandwidth on your end so that you can connect
easily and
without internet.
It allows to minimize the bandwidth on your end so that you can connect
easily and
without internet.
 It prevents other people with malicious intentions from hacking it to
access your
personal data. While this generally goes unnoticed, WiFi hotspots are increasingly targeted
by
cybercrime.
It prevents other people with malicious intentions from hacking it to
access your
personal data. While this generally goes unnoticed, WiFi hotspots are increasingly targeted
by
cybercrime.
Now you know that a WiFi network is very risky and facing multiple attacks, let's talk about some tips and precautions to be taken to safely access the internet when you are traveling.
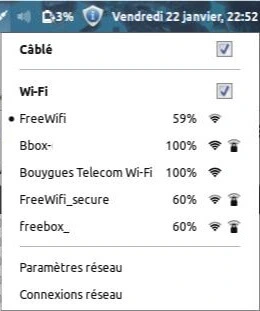
When purchasing the internet box or any other WiFi router, these have generic names given to them by the manufacturer. By adapting the name of your WiFi, you make it difficult to detect. This is a configuration that is possible for all boxes. Even when you set up your phone and turn it into a hotspot.
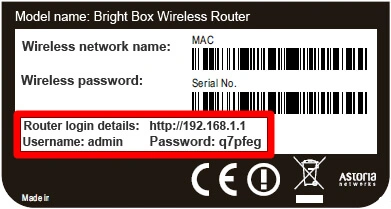
WiFi networks can be protected by a password. Even if there are some that have free access, when the WiFi boxes are delivered, access to the network is generally protected by a generic password. One of your first instincts after to change the name of your WiFi is of course changing the password to personalize it. The WiFi password is generally at least 8 characters long. For better security, it is recommended not to use personal information such as:
 The birth date;
The birth date;
 The wedding date;
The wedding date;
 The parent's name;
The parent's name;
 Or even the usual references to your everyday life.
Or even the usual references to your everyday life.
You need to make sure you find a combination of upper and lower case letters and numbers with some special characters.

It is also one of the most useful solutions for securing WiFi. An inconspicuous WiFi hotspot will be significantly less exposed. This is a feature that is generally offered. In this way, to connect to WiFi, which is now invisible, the owner must enter the exact name of the WiFi himself before being able to connect to it. It is therefore necessary to know the name of the WiFi by heart.

It is possible to process data that passes through WiFi. In this way, users of a WiFi network will be able to ensure that their information cannot be collected by a person with bad intentions. In the context there are two encryption keys that are used. These are the WEP and WPA security keys.
The WEP key is generally used for basic protection in the context of securing WiFi networks. It is longer and better constituted than a classic password. It consists of 10 to 26 characters. It will offer you the advantage of encrypting your data which will be broadcast through the WiFi hotspot. The configuration is generally available in most boxes offered by access providers.
However, it should be noted that this security key can be easily broken by a seasoned hacker. This is why there is the other alternative: The WPA key.
The WPA key for "WiFi Protected Access", is a much more powerful data encryption tool than the previous key. However, not all standard users can use it due to its somewhat complex nature. It has been designed to provide an additional layer of security to the WiFi network. It also allows the encryption of data passing through the protected WiFi network. Today, most routers use it. Its activation is foreseen in the parameters of the WiFi boxes which are made available by the access providers. It essentially consists of 8 to 63 characters. In other words, much longer than the WEP protocol. Unlike the latter, it is difficult for hackers to find the WPA protocol and crack it easily.
Many passwords which are difficult to hack are created of letters, numbers and special characters. Complex passwords composed of a string of characters are therefore more difficult to remember for users. But they are also much easier to hack. Because, in reality, the sequences of characters chosen by Internet users are far from being random. It means that the hacking algorithms can easily "crack" this security in a very short time (from a few minutes to a few days).
The solution to create a secure password is provided. We recommend using a string of words that is unconnected but easy to remember. For example: mywifipassword.
According to calculations made by the institute, it would take more than 500 years for hackers to succeed in hacking this password.
Securing your WiFi network is a substantial undertaking, but it is absolutely crucial. That's why it's imperative that you take the initiative and do everything in your power to ensure your protection. To assist you in this endeavor, we present PASS WIFI software, a program that has already demonstrated its effectiveness. This software allows you to analyze nearby WiFi networks and retrieve their passwords. Beyond aiding in testing the security of your hotspot, PASS WIFI is currently the only program that grants you unrestricted wireless access. This can be done anytime, anywhere, right from your smartphone or computer.
Abdalla Al Ali, Chief Police Officer, Dubai Police Force