Hack TikTok account
The best hacking techniques

Hack TikTok account
The best hacking techniques

The IT security of social media accounts remains one of our highest priorities as users. Indeed, when we examine the most used platforms, social networks occupy a preponderant place, with TikTok appearing well among the top 5.
This article is intended to be a tutorial to learn how to hack a TikTok account. Rather, it aims to help you better understand the threat, by providing you with advice to protect yourself and avoid any risk of exposure.
First of all, it is crucial to understand that TikTok is not just a source of entertainment. For many people, it is a source of income. Additionally, as a social network, TikTok contains personal data that could be exploited for nefarious purposes, such as identity theft, hijacking of online accounts or theft of money.
Hack a TikTok password can meet various needs, thus emphasizing the need to protect oneself.
We will describe proven methods that continue to be used by TikTok account hackers.
There are several hacking methods. We have very popular techniques that are well known to the general public, these are methods that have already been the subject of several publications, warnings and warnings. Beyond these popular techniques, there are lesser-known methods that you've probably never heard of.
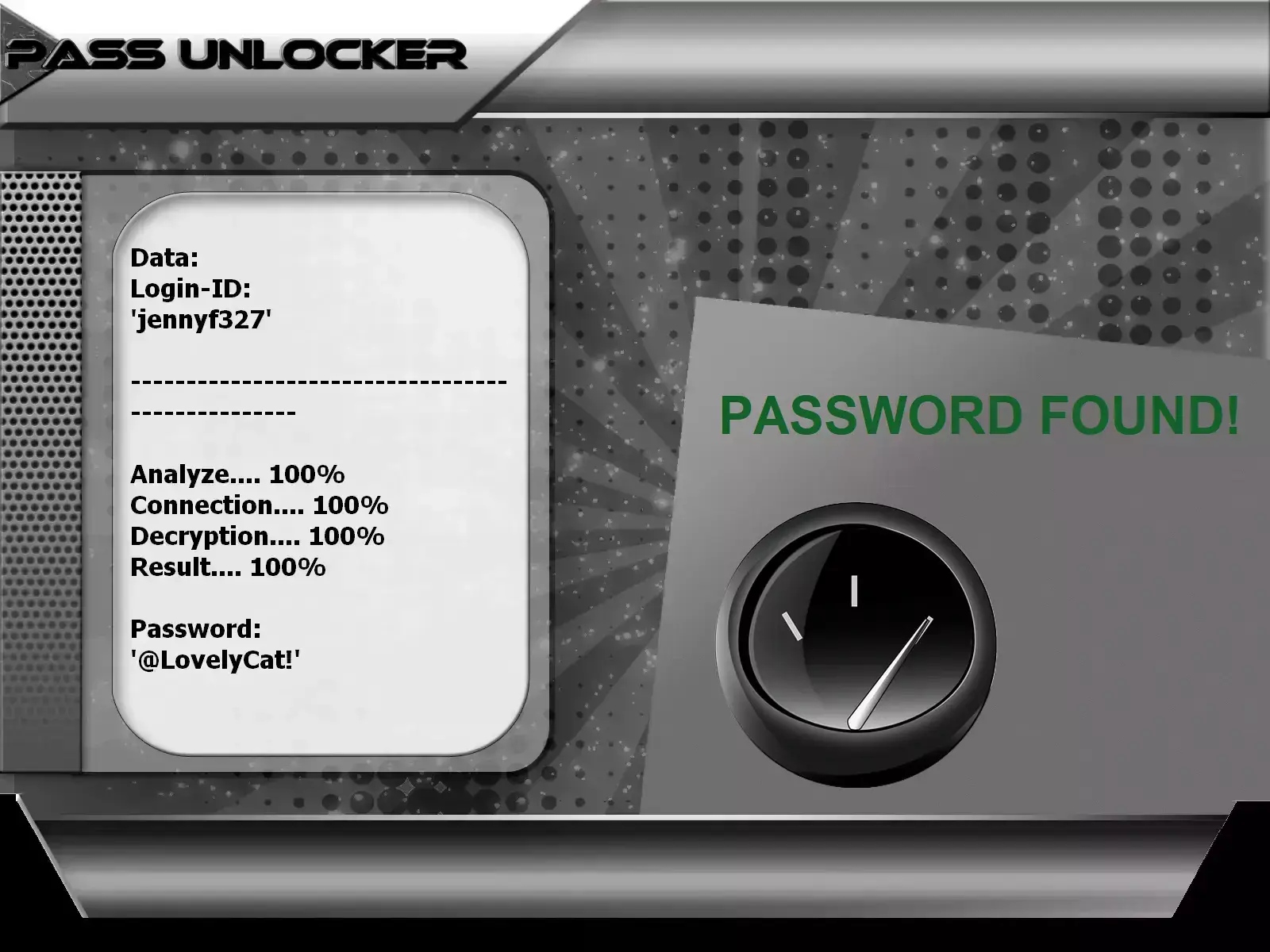
with PASS UNLOCKER
This app is best for being able to reveal TikTok passwords from a @username, phone number or email address. By entering one of these three pieces of information, PASS UNLOCKER will be able to decipher and display the password on your screen, allowing you to connect to the TikTok account without difficulty.
You can download PASS UNLOCKER from its official website: https://www.passwordrevelator.net/en/passunlocker

If there is one technique widely used by hackers to steal login credentials and hijack online accounts, it is undoubtedly phishing.
The phishing technique consists of sending a link to the target, contained in a standard message inviting them to perform a particular task. In our context, this could involve impersonating TikTok by asking the target to fill out a form requiring their login credentials, for example. Another possibility is to make the target believe that they are the victim of a hack and that they should quickly change their login credentials. Following this message, a link inviting them to validate the modification will allow them to have their connection credentials stolen.
We have all been targeted by this type of message at least once, so be vigilant now.

Recovering a password requires decryption, analysis and deduction. There are several ways to crack a password.
First of all, we have the brute force method, which involves randomly generating several combinations of letters, words and symbols, trying them one by one to find the right one. This process is automated using special software or suitable scripts. Depending on the difficulty of the password, the attack may succeed immediately or take several days. It is important to note that the computing power of the device used plays a crucial role in its effectiveness.
Dictionary attack is another password recovery method:
The dictionary attack involves grouping together all kinds of combinations, known as potential passwords. These combinations may be based on user habits or passwords obtained through leaked databases. This grouping is called a dictionary and thanks to this, the hacker filters the information until he finds the personal data of interest.

We can't talk about account hacking without talking about spyware. As their name suggests, these are computer programs intended to exfiltrate information of any kind without the victim's knowledge. For stealing login credentials, they are very effective.
Malware is installed on the terminals of targeted people before being operational. Their installation can be done remotely or manually.
Among the most used spyware, we have keylogger, a keylogger. Its function is to collect all the information entered by the keyboard of the contaminated terminal. Once this information is collected, it is sent directly to the spyware operator. This method cannot be used against devices that use numeric keypads. To counter this limitation, hackers have developed software that spy on the screen, called screen recorders. These software allow you to monitor the activity taking place on the device screen, thus providing a solution to this limitation.

Social engineering is a common method but often overlooked by potential victims. Often, when we talk about hacking, we automatically think of the use of complex means, long lines of code or sophisticated software. However, simple ways exist and social engineering is a clear example. In this method, the hacker simply attempts to collect various information about his target by establishing contact through social media or other means. The goal is to ask questions to elicit information, capitalizing on the fact that most of us create passwords based on information from our daily lives. So, asking for your loved ones' names, date of birth, or other information can help find your password. Even simple questions such as your dog's name can be exploited, so be careful.

Whether to make a contactless purchase or access a specific platform, QR code scanning has become common practice. However, this democratization of QR codes has also attracted the attention of cybercriminals. They replace QR codes in public places with similar codes that redirect their victims to fake platforms, a kind of QR code phishing. Although the idea is similar to phishing, this time it's not a link you click on.

This technique is well known. It involves the use of a fake WiFi network to trick users. When we are in a public place, we all tend to look for a free Internet connection, usually the one in the specific location we are at. In this context, it is easy to trap ourselves. The cybercriminal simply deploys a WiFi network that he controls. On every connection, it can collect data by injecting automatic but malicious scripts.

This is a method of stealing a target's phone number with the intention of using it for malicious purposes. If you are wondering how stealing a phone number can help crack a TikTok password, here is the explanation. Generally, our online accounts are associated with our telephone numbers, allowing us to reset the password if necessary. During the reset process, a unique code is sent via message to the user's phone number. This code authenticates their identity and allows them to change their password. In other words, with access to your phone number, any hacker can hijack your online account.
You may be wondering how a hacker can steal someone else's phone number. It's important to note that this technique has been used before, with one of the most famous victims being former Twitter executive Jack Dorsey.
First of all, the criminal must have sufficient personal information about his target, such as first and last names, date of birth and other elements that can be collected on social networks. Once this information is gathered, the hacker remotely contacts the telephone operator posing as the victim and providing all the necessary information. When the identity is confirmed, the operator asks to retrieve the phone number from a new SIM card delivered to it. To do this, the hacker can cite a failure of their current SIM card or claim to have lost their phone. Once the identity is confirmed, the telephone operator transfers the phone number, allowing the hacker to take control.
In view of the above, it is important to recognize that the use of TikTok can potentially expose users to hacking risks. Hacking methods are varied and at any time, cybercriminals can exploit the site's vulnerabilities. Therefore, it is imperative to take steps to strengthen your online security.
Whether for a TikTok account or any other account on social networks, users must think about protection when creating their accounts. This allows them to make necessary arrangements. However, it is essential to be realistic: no protection measure is 100% effective, but some provisions can make it very difficult for hackers, unless you are a master of stealth.
Protecting against hacking involves constant awareness of cybersecurity best practices. Here are some recommendations to strengthen your online security:

Double authentication is an additional security measure to strengthen your identification. It consists of creating a second layer of protection: after entering your classic connection details (username and password), a second code is required, generally sent by message or e-mail. This code is often single-use. You can also use apps like Google Authenticator or Microsoft Authenticator, or even key-based dual authentication methods.
Discretion is a great quality when on social media or the internet in general, even if it sounds like the classic advice from your mother or child. Being constantly present means you're probably sharing too much information about yourself, sometimes without even realizing it. Whether it is your location, the place of your last appointments, the birthday of a loved one, or the name of your primary establishment, all this information can be used against you. Be sure to limit the amount of information you post, avoid posting photos that suggest location unless you are an influencer and be selective in your responses and comments.
Third-party apps are designed to improve the user experience by offering additional features, but you're often unaware of where they come from and what they do with your data. These apps may collect personal data that can be used for malicious purposes. It is therefore recommended to avoid using third-party applications as much as possible.

Security updates are crucial for user protection. Whether they are security vulnerabilities in software or integrated into computer hardware, their discovery by hackers can pose problems. Faced with an active market for the sale of security vulnerabilities, the best way to fight against vulnerabilities is to regularly update your system. Many users overlook these updates, but a missed update can open a door to hacking. So pay attention to update notifications and possibly enable automatic updates.

Antivirus software is used to protect you from malware, as a large part of computer hacking methods rely on software of this type. The antivirus then has the task of protecting you in order to prevent this type of situation. You are fortunate to be able to easily access this type of program at a lower cost today. There are some for any type of device. There are even some that are free and very effective. Don't hesitate and if you don't already have an antivirus, automatically look into getting it.

Virtual private networks are now democratized. Luckily, there is no shortage of offers on the market and you can therefore obtain them at suitable prices according to your needs. The advantage with the virtual private network is being able to connect to the Internet all the time, while preserving a certain confidentiality. You will have the possibility of not being followed by anyone, above all to protect yourself from session hijackings.

No security measures are necessary or useful if anyone can access your computer terminal, whether it is your computer, your smartphone, or even a tablet. Please lock access so that anyone cannot use it without your consent. Preferably, use biometric protection measures. Fingerprint or facial recognition will certainly do the trick.

Nowadays, a good password is made up of several different characters, namely symbols, upper and lower case letters and of course numbers. A good password is at least 8 characters long. Furthermore, stringing together several combinations of letters, numbers and symbols does not protect you, especially if they are elements relating to your date of birth, your first and last name, or even things that relate to your private life. In other words, no private information in your password. Choose random characters. If necessary, opt for one sentence.
Additionally, it is recommended not to use the same password on multiple accounts at once. This need is explained by the fact that you are not protected from a data leak from one of the platforms on which you are registered. In this kind of situation, all of your accounts are exposed if you make this mistake, the mistake of using the same password for multiple accounts.

As we mentioned above, humans are not perfect, so no security measure is absolute. It is important to remain vigilant no matter what you say. Remember that every time you log in, you are more exposed to account takeovers. This means you need to stay informed about new threats happening at all times. You should avoid using public Internet networks as much as possible, exposing your personal information to everyone and especially not being too careless with basic security measures. Be vigilant in your interactions on social networks to protect your TikTok account against hacking. If you feel that you are vulnerable, do not hesitate to contact professionals. They can certainly help you strengthen your online security.
If your account is hacked and you lose access to your TikTok profile, our PASS UNLOCKER app will be able to help you regain access to your account.
TikTok hacking refers to unauthorized access to TikTok accounts through various techniques such as phishing, spyware, social engineering and more.
Concerns about TikTok hacking arise due to potential misuse of personal data, identity theft, or financial loss. As TikTok is a popular social media platform, it becomes a target for cybercriminals.
To protect your TikTok account, you can use measures like enabling two-factor authentication, avoiding third-party apps, running security updates, using antiviruses, employing VPNs, securing access to your device, using strong and unique passwords and staying vigilant.
Two-factor authentication adds an extra layer of security to your account by requiring a second form of verification, usually a code sent via SMS or email, in addition to your password.
It is recommended to avoid using third-party apps with TikTok as they may compromise your account's security by collecting personal data or introducing vulnerabilities.
You should regularly check for and install security updates on your devices to stay protected against potential vulnerabilities. Enabling automatic updates can ensure timely security patches.
A VPN (Virtual Private Network) encrypts your internet connection, providing anonymity and security by routing your connection through remote servers. This protects your data from interception and enhances privacy.
Strong, unique passwords are essential to prevent unauthorized access to your accounts. They should be complex and not easily guessable and using different passwords for each account reduces the risk of multiple accounts being compromised in case of a data breach.
If you suspect your TikTok account is hacked, you should immediately change your password, enable two-factor authentication, review your account activity for any unauthorized actions and contact TikTok support for assistance.
Professionals can offer services such as security audits, risk assessments and implementation of robust security measures tailored to your specific needs. They can also provide guidance on cybersecurity best practices and help mitigate potential threats.