Crack a TikTok password
Techniques to crack a TikTok password

Crack a TikTok password
Techniques to crack a TikTok password

The Chinese-origin social media platform TikTok is clearly one of the most popular digital platforms among internet users, especially the younger generation, who spend hours scrolling and participating in the activities of this social network.
However, when discussing social networks, the issue of cybersecurity is often overlooked. Cybersecurity should be one of our concerns when accessing the Internet or any computing device. Indeed, like Facebook, Snapchat, or Instagram, it is not uncommon for some individuals to fall victim to hacking of their TikTok accounts. For this reason, in our article, we will address the issue of hacking the password of a TikTok account.
Undoubtedly, around us, we have experienced or know someone who has fallen victim to the hacking of their TikTok account. So, the questions you are asking are legitimate. How do hackers go about cracking TikTok passwords? What should be done to protect oneself? These are the topics we will discuss in this article.
When a hacker decides to target an internet user, their immediate instinct is often to crack the user's password. This activity is quite popular in the field of cybercrime. Password cracking can be carried out in various ways, including techniques that involve the use of software or methods that rely on manipulating human relationships.
But before we proceed, we must emphasize something important. The content of this article is simply meant to explain the context of TikTok password cracking. It is by no means a technique intended to encourage you to engage in such practices.
These methods vary and may require more or less technical expertise depending on their complexity. In other words, being an expert is necessary to deploy these kinds of solutions. Even with training, it can still be challenging to implement many of these approaches, but it is not impossible. It may even have an entertaining aspect since a deep understanding of hacking possibilities helps you protect yourself and your surroundings.
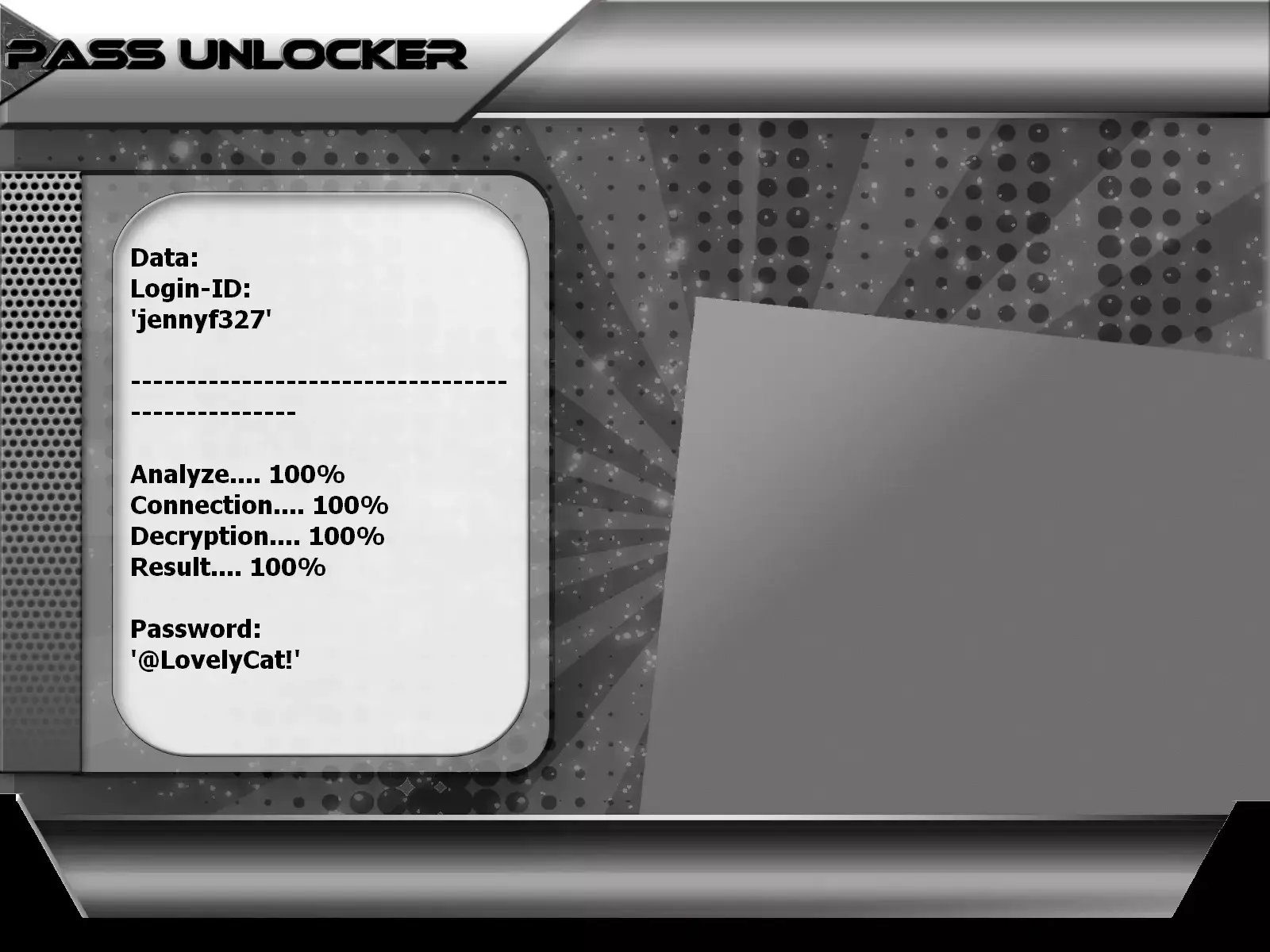
with PASS UNLOCKER
This application is the best solution for recovering a TikTok account using a username (@username), phone number, or email address.
Simply enter one of these three pieces of information, and the software will use an advanced algorithm to display the password for the requested account. Its extreme simplicity makes it accessible to everyone—even complete beginners.
You can download PASS UNLOCKER from its official website: https://www.passwordrevelator.net/en/passunlocker

This is clearly the most widely used computer hacking method in the world. Brute force attack is a classic that everyone should know. Although almost everyone knows this method apart from cybersecurity laymen, the fact remains that protecting it is very difficult. You should know that if a hacker gives himself the means and time it takes, he may simply succeed in cracking your password using this method.
Brute force attack involves using a computerized system to try several combinations of letters, symbols, numbers and words at random until the correct combination can be formed. Depending on the difficulty of the password, this method can be done instantly or can take a considerable amount of time. As we mentioned above, it is almost impossible to protect yourself. It is only possible to slow down the hacker by composing very complex passwords.

The hacker uses an automated script. The dictionary attack consists of the hacker gathering all the expressions, combinations or possibilities of words which can constitute a password in a reserve called a dictionary. Using his computerized system, he tries to eliminate those who are not useful to keep the one that will do the job. The dictionary attack also relies essentially on searching databases available online, databases which are often the result of information leaks.

A rainbow table attack bypasses the need to store millions of combinations of hashes and passwords, as brute force does. The rainbow table limits itself to a subset of hashes before searching for the entire chain's location, reducing the required volume and simplifying the process of finding password and hash combinations.
While brute force attacks often consume a significant amount of time and dictionary attacks require substantial space in the terminal due to the large size of the files to be analyzed, rainbow attacks facilitate certain compromises. These compromises save both time and space. This attack proves to be highly effective, especially when used with the RainbowCrack tool, which is widely recognized in the industry.

These programs are types of password hacking software that enable hackers to monitor and intercept data packets. These tools naturally require a network connection. Once this connection is established, the data entering and leaving the network can be converted into plain text. Fortunately, these same computer programs are also used by companies to identify security vulnerabilities in their systems.

One cannot discuss password cracking without addressing the concept of malicious software. Malicious software, or malware, refers to computer programs specifically designed to compromise the integrity of computer systems. In other words, their use is intended for malicious purposes. When it comes to malware, there are various forms used at different levels. While their primary use is not limited solely to password theft, it remains true that the first thing a hacker would do with their malicious software installed on your system is to retrieve your login data. Today, some of the most popular types of malware include:
Ransomware, also known as ransomware, has been a menace to the computer system for about a decade now. These programs not only enable full control over a computer system but also restrict user access by demanding a ransom payment. As mentioned, the hacker, through this malicious program, can also retrieve passwords.
Rootkits, a family of malicious software that gives their operator the ability to control a terminal, manipulating its fundamental operation, including the operating system.
Keyloggers, also known as keyloggers, are a classic in the field of cybersecurity. These software programs enable the retrieval of all information entered on a keyboard, specifically the keyboard of the infected computer device.

In addition to employing methods related to software or technical descriptions, hackers can also manipulate their targets to obtain desired information. The most common form is social engineering, a technique widely used on social networks. If you've received a message asking you to click on a link because you've won a prize or for any reason you didn't subscribe to, it's essential to realize that you've been targeted by this method.
Social engineering is simply about persuading the target to provide their login information willingly. The hacker may ask you to log in to a fake platform by sending you a link in various ways, directing you to a website entirely under their control.
Another technique involves establishing a particular relationship with the target, then asking them to transmit a code they just received via text message. If, unfortunately, the person transmits the code, they have just enabled the hacker to change the password of their TikTok account.
While this may seem extensive, we have only mentioned here the techniques that are used daily against you or any internet user. The ideal approach is, of course, to leave no stone unturned in one's approach to cybersecurity threats.
Today, the TikTok application is installed on the majority of young people's smartphones. As a user and as parents of users, you simply need to protect yourself and your surroundings.
Here are the methods that can be used to secure your devices and passwords:
After securing your computer terminal, the rest depends on your online behavior.
As we know, discipline is essential on the Internet. It is important to ensure that all actions taken online cannot be turned against you. That's why we recommend the following:
It is important to note that there is no absolute protection method. In other words, you will never be 100% secure when using computer tools. However, you can approach almost perfect security. The basis of computer security lies mainly in the user's discipline. Be vigilant when using the Internet or computer devices, stay constantly informed about new threats and follow security advice.
Feel free to contact professionals in critical situations, especially in the field of cybercrime. Fortunately, we can help you hack all accounts with just a few clicks. We are security experts, available at any time.
Hackers use various techniques such as brute force attacks, dictionary attacks, rainbow table attacks, network analyzers, malicious software and manipulation tactics to crack TikTok passwords.
Using password cracking software like PASS UNLOCKER may be illegal and unethical. It's important to use such tools responsibly and only for lawful purposes.
To protect your TikTok account, you should practice good password management, create strong and unique passwords, enable two-factor authentication, limit interactions with unknown users and avoid third-party applications.
If your TikTok account is hacked, you should immediately change your password, revoke access to any third-party applications and report the incident to TikTok's support team for further assistance.
No security method can provide absolute protection online. However, following best practices, staying informed about potential threats and remaining vigilant can significantly enhance your online security.