Hack a TikTok Password
Effective methods that work

Hack a TikTok Password
Effective methods that work

TikTok is the most used social network in the world among young people. It accumulates billions of users every month and stands out with Facebook as one of the most used digital platforms in the world.
The main functionality of TikTok is to share short videos covering different subject areas. These can be fun, educational, political or informational videos. The popularity of the platform does not only attract simple users who want to have fun, there are also people with bad intentions who are getting closer and closer to this platform with the aim of causing harm. Just like online access platforms, the social network requires the use of login credentials.
In this article, we will discuss the concept of hacking TikTok account passwords. First of all, we want to mention that the objective of this article is not to encourage you to hack. We want to teach you the different dangers to which each user, if you are one of them, is exposed. Knowing these dangers will obviously allow you to know how to protect yourself and ensure the confidentiality of your personal data.
There is an anthology of techniques that should not be overlooked and we have gathered for you the most effective techniques that can hack TikTok accounts. We will proceed methodically starting from the most popular to the least popular. Please note that we will give you appropriate advice to better protect yourself.
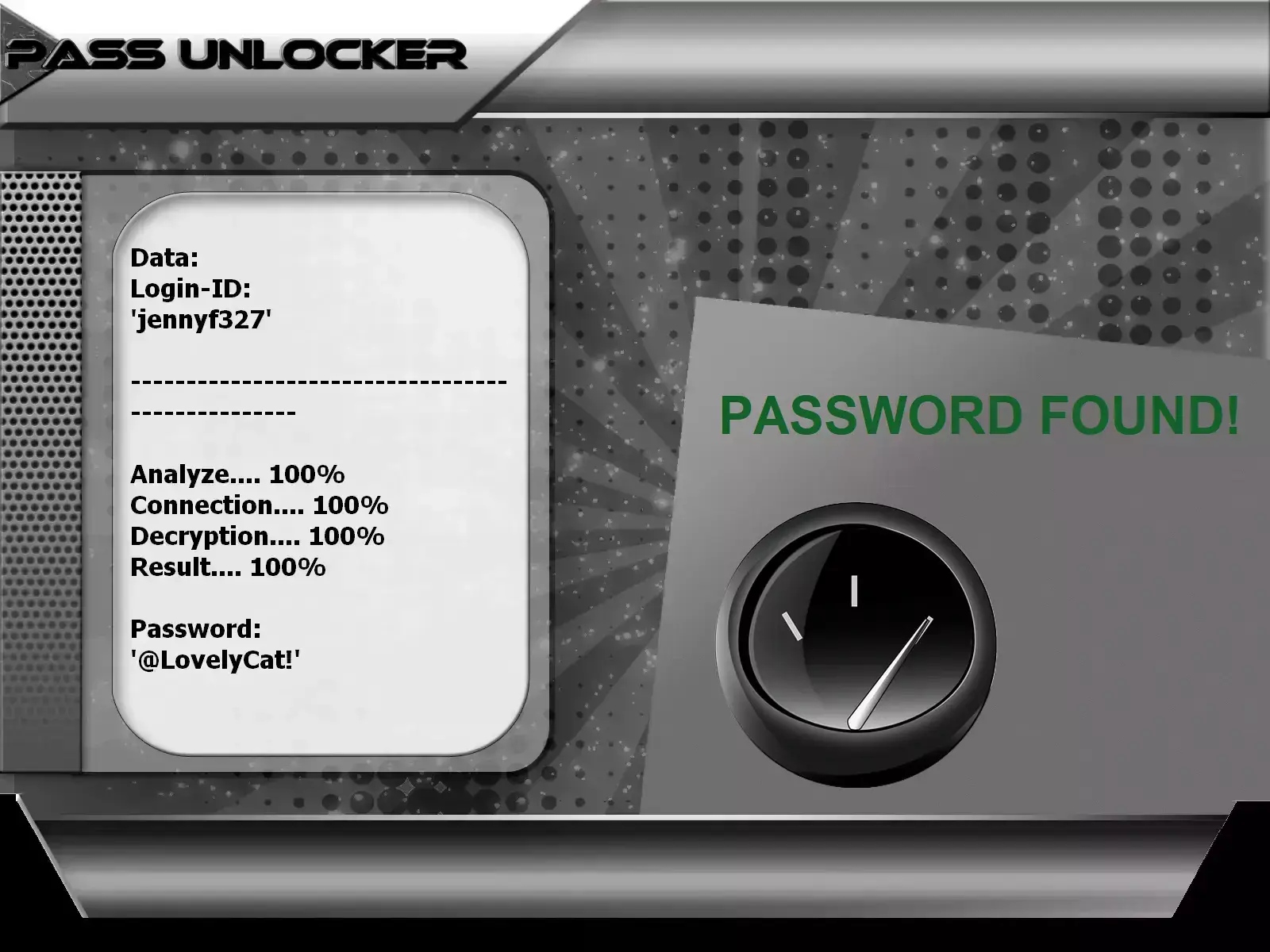
with PASS UNLOCKER
This application allows you to hack any TikTok password from a @username, phone number or email address. From one of these 3 pieces of information, PASS UNLOCKER will decrypt and display the password on your screen. You will then be able to log in to the account without difficulty.
You can download PASS UNLOCKER from its official website: https://www.passwordrevelator.net/en/passunlocker
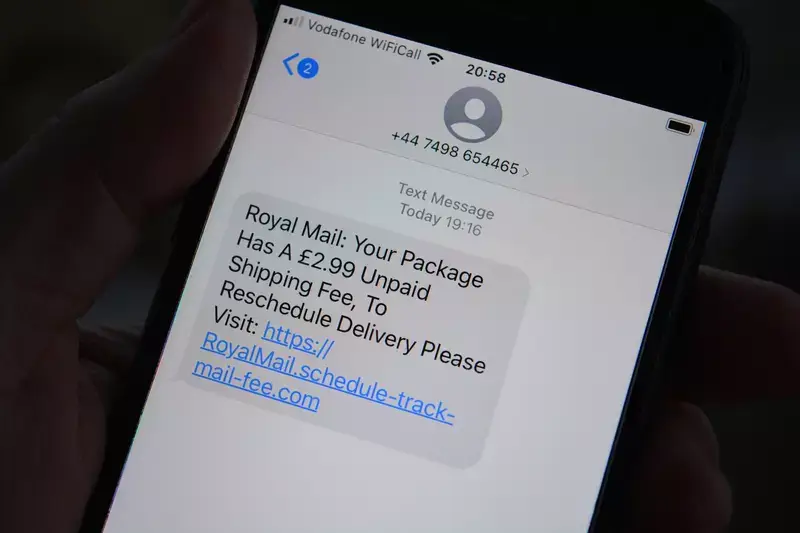
When we talk about computer hacking, specifically password theft, the first technique that comes to mind is necessarily phishing. This is a fairly basic and popular technique in the field of cybercrime. Almost the majority of computer attacks have used this method.
At first glance, this method requires having a certain contact with the target because it simply consists of pushing the latter to commit the mistake which will allow him to expose his password. In general, hackers will send messages to their target (people or companies). They will encourage the user to click on a link in order to register on a website. Unsuspectingly, when he performs this action, he quickly falls into the trap, because the link redirects him to a fictitious digital platform. This platform is manipulated directly by hackers. By providing the requested information in the fields, the inattentive user provides direct access to their password. In summary, here is what phishing involves.

Social engineering is a method which consists of exploiting relationships with your target in order to extort as much personal information as possible. You can be friends on social media or even in real life. In this method, the hacker will simply try to collect as much information about you as possible. As they know that users use a lot of passwords that are based on personal data such as dates of birth or the names of relatives, the hacker collects information of this type. When he has his information, he will then try to guess the password by making random combinations.
There is also the technique of pretending to be a friend of your target. The hacker initiates a password reset process. He then asks his target to send him a code that he received by message, making him believe that he entered the wrong number. The code is the two-factor authentication security message. By sending this code, the victim user gives this hacker the opportunity to change the password and deprive him of access to his TikTok account. A fairly simple method but which has already proven its effectiveness and which it continues to prove.

The technique of cracking your TikTok password is part of several methods that we can describe. As the name suggests, the goal is to force access and find the password whatever it takes.
Still in the classics of cybercrime, we have pirate software called the keylogger. Its particularity consists of recovering all the information that a person enters on the keyboard of their computer terminal. Whether it is a smartphone, a computer or even a tablet, when the computer program is already installed on it, the operator in charge of this malware can simply retrieve any information that will be useful to him. And among the lot, there is of course your password.
Obviously, this technique is not perfect because it mainly works on computing devices that operate using physical keyboards. Since the device uses a numeric keypad, the software becomes unusable. To counter this weakness, the screen recorder was then invented. The screen result is not necessarily pirate software since it is already pre-installed in the majority of smartphones, computers or tablets in circulation. The problem is that hackers can use this feature to steal your data. Among the information, everything you do on your screen will be copied and sent to your hacker.
Which means that when you use your smartphone to log into TikTok by typing the code on the screen, you will then be exposed.

A technique that is somewhat unknown to the general public, SIM Swap appears to be something very delicate. This is not hacking in the true sense of the word. It is a practice which consists of hijacking the telephone number of a third party by using certain vulnerabilities in the system.
As you know, mobile operators nowadays offer online services. These online services give customers the opportunity to resolve certain problems online. For example, recovering your telephone number following the disappearance of your phone without even leaving your home.
This is how the hacker will proceed to steal your phone number. First, it will call your telephone company. He impersonated you by providing certain personal data about you. Obviously, data that he took care to collect on the Internet or even from you directly. Once the telephone operator is fooled by this identity theft, the criminal then asks to recover his telephone number on a new SIM card. It goes without saying that the phone number is yours, but it will be sent to the hacker from now on. You then lose access to your telephone number. As if that wasn't enough, the hacker who has your number can then proceed to change your password on your online accounts. This is exactly why this method, which nevertheless seems very simple, is dangerous.
Like the previous method which is SIM Swap, Simjacking also exploits certain security vulnerabilities relating to SIM cards. SIM cards are not just small chips, they are also a concentrate of technology with their own operating system. Who says operating system necessarily says vulnerability! The problem is that there are many SIM cards produced for a very long time that have not been updated and hackers know this.
Using scripts specialized in exploiting this type of vulnerability, they will simply try to corrupt the SIM card in order to extract any type of information that seems necessary to them and this technique works perfectly.

Session hijacking is a method reserved for specialists. In this technique, hackers use sneaky methods to hijack your connection. For example, if you go to Google or you have access to your phone, your goal is to, for example, go to TikTok. Through strategic manipulations, they automatically take you to another platform. Although the process has similarities to social engineering, hackers are not forced to explicitly trick you into clicking a link. They have a variety of methods, including:
WiFi is omnipresent these days, contributing to the democratization of Internet access. Although it makes connection easier and cheaper to use, it also represents a breeding ground for hackers seeking to trap users. Indeed, the appeal of WiFi networks offering free Internet access is universal. However, not all open WiFi networks are secure. Hackers can deploy fake WiFi networks or tamper with existing networks, exploiting vulnerabilities in your connection. When you use these networks to access your online accounts, your data may be discreetly collected without your knowledge.
This is a somewhat recent technique which is a twisted form of phishing. Unlike the first method that we mentioned above, which consists of tricking the user by sending them a link, quishing is a technique that pushes the user to go to fake platforms after scanning QR codes. As we know, the use of QR codes has become very popular in recent years, particularly since the coronavirus pandemic. Today, we scan QR codes for almost everything. So, hackers had the brilliant idea of often modifying QR codes with fake ones. So, the average user goes to a space to carry out a transaction. By wanting to scan the QR code indicated, he can make a mistake and be fooled by the hackers' fake QR code. Which will obviously lead him to a fake platform where his information will be requested. Obviously, the moment he grabs them, hackers will simply collect them and use them. A method which unfortunately claims more and more victims because of our habits with QR codes.
In view of the above, we can mention that simply using TikTok exposes you to hacking. There are many hacking techniques and at any time, the cybercriminal knows how to take advantage of the site's flaws. So, you also need to protect yourself.
Protecting your profile requires a lot of discipline and action. Here are some tips you can put into practice to achieve this goal:

If you use a smartphone or tablet to access TikTok, it is essential for you to find a way to secure the device in question. For this, you need to use antivirus protection software. It is essential because one of the biggest threats is malware. Fortunately for you, there are several types of protection, antivirus software adapted according to budgets. In this case, do not hesitate to protect your device and deploy the essential tool for that.
Securing your device is more than just installing antivirus. You will also need to ensure that anyone cannot use it without your knowledge or consent. To do this, you simply need to lock access using a biometric method (fingerprint or facial recognition). Then use devices that offer you such security. Also be careful not to leave it anywhere, even if it's only for a few seconds.

The VPN is a network that gives the possibility of securing your care connection because it escapes certain abuses on the Internet. Among the abuses, there is also session hijacking or connection spying. VPN networks have become more popular in recent years, which gives you the possibility of easily having a subscription at a very reduced cost. You can connect to the Internet without risk of being tracked.

If you are tempted to connect to the Internet for free when in public places, it is important to avoid any network. Some WiFi hotspots are traps. Access is freely open to anyone. Even if you have all the necessary security, this security is also essential because you cannot know what malicious strategies the hacker has.

Public devices are often infested with malware. If this allows you to often have simple access to your online accounts when your terminal is unavailable, be aware that the risk of being fooled and being a victim of password theft is very great when you use a device audience. Just avoid it. By public device, we are referring to internet cafe computers or professional computers that you can use at work. You should also avoid using computers belonging to relatives because you never know...

The password is the essential identifier that the hacker targets when he decides to attack you. Therefore, you should be careful when making up your password. Put it in optimal priority: the password must consist of at least 8 characters. These characters should be varied between numbers, symbols and even letters. The second priority lies in the use of personal data. It is completely forbidden to use information that is likely to be too familiar. For example, don't use your name or the name of a loved one. Also, don't use dates of birth or numbers relating to your habits. Preferably use data that is completely foreign to your social situation. Also use sentences, as they are more complex and difficult to break.

Don't use the same password on all your online accounts. Indeed, if this is what the majority of us do, you should know that hackers already know how to take advantage of such situations. Furthermore, since you are not safe from a data leak, the fact that one of your accounts is exposed to hacking because of a probable leak exposes any of your accounts . Therefore, you must be disciplined.

No matter how difficult your password is, you are not safe from a leak, as we mentioned above. You are also not protected from any error which could expose you. Consequently, double authentication protects you doubly and allows you to anticipate potential hacking of your TikTok account. Luckily for you, the social network offers this authentication method. It should then be activated as soon as possible if this has not already been done.
In the event of your TikTok password being hacked, if you unfortunately find yourself the victim of an attack allowing an intruder to take control of your account without your knowledge, we have developed a suitable solution. Our PASS UNLOCKER tool is specially designed to help you regain control of your TikTok account.
PASS UNLOCKER's main mission is to restore access to any hacked TikTok account. We put this tool at your disposal to help you overcome the unfortunate consequences of a possible intrusion.
Hacking TikTok passwords or any other online account without proper authorization is illegal and unethical. Engaging in such activities can lead to severe legal consequences.
No, hacking techniques should not be used for any purpose without proper authorization. Ethical hacking involves obtaining permission from the owner of the system or account before attempting to test its security.
There are several measures you can take to protect your TikTok account, including using strong, unique passwords, enabling two-factor authentication, avoiding suspicious links or downloads and being cautious about sharing personal information online.
If you suspect that your TikTok account has been hacked, you should immediately change your password, revoke access to any third-party applications and report the incident to TikTok's support team for further assistance.
Yes, if you have forgotten your TikTok password, you can use the official password recovery mechanisms provided by TikTok. This usually involves receiving a password reset link or code via email or SMS.
Yes, TikTok and other online platforms often provide official password recovery tools or services. It's important to only use these authorized methods to avoid falling victim to scams or unauthorized access attempts.
If you encounter any suspicious activity or believe there is a security threat on TikTok, you should report it immediately to TikTok's support or security team. They will investigate the issue and take appropriate action to mitigate any risks.